New updated Lead4Pass 200-901 Dumps with PDF file and VCE practice exam engine to help pass the 200-901 DEVASC Exam successfully!
Lead4Pass 200-901 exam dumps contain 294 exam questions and answers, covering complete DevNet Associate 200-901 DEVASC certification exam questions, and verified to be true and valid, check here to get the latest Lead4Pass 200-901 dumps: https://www.leads4pass.com/200-901.html (PDF+VCE).
And, download a partial Lead4Pass 200-901 dumps from Google Drive: https://drive.google.com/file/d/1S703FS0ZIL8hCjwTblU0_nENeTuO33Fy/
Also, read the latest 10 Lead4Pass 200-901 dumps questions and answers online:
| Number of exam questions | Exam name | From | Release time | Previous issue |
| 13 | Developing Applications and Automating Workflows using Cisco Platforms (DEVASC) | Lead4Pass | Sep 24, 2022 | [Updated July 5, 2022] 200-901 dumps questions |
New Question 1:
Which platform is run directly on top of a hypervisor?
A. bare metal systems
B. virtual machines
C. containers
D. applications
Correct Answer: B
New Question 2:
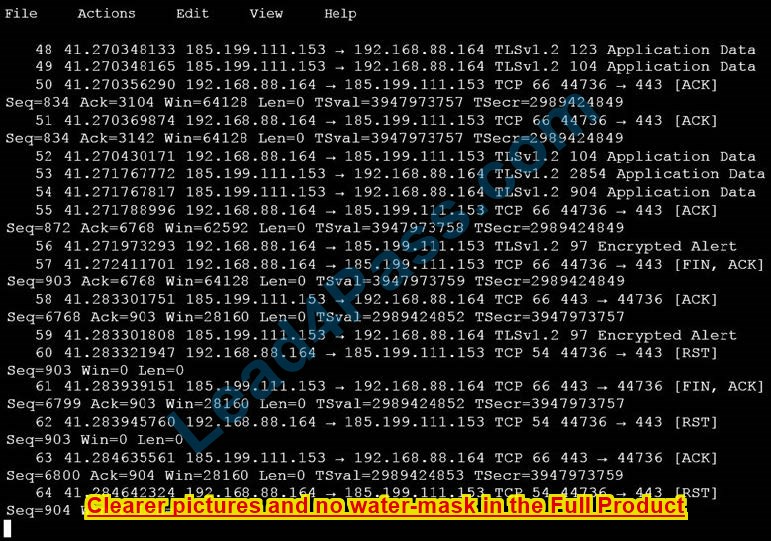
Refer to the exhibit. A collaboration engineer has developed a script to automate the gathering of information by providing the email address of the individual. When the engineer tests the script, a 401 error is received. Which command fixes the script?
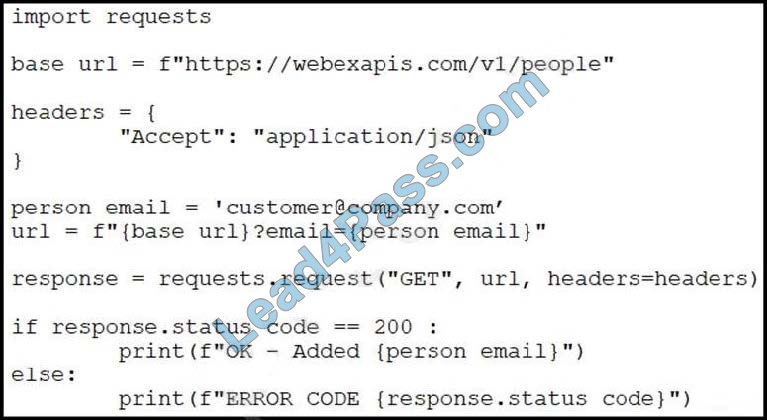
A. Add “Authorization”: “Bearer ” to the headers.
B. Add “Authentication”: “Basic ” in the base_url after “HTTPS://”.
C. Add “:@” in the base_url after “HTTPS://”.
D. Add “Authentication”: “Bearer ” to the headers.
Correct Answer: A
New Question 3:
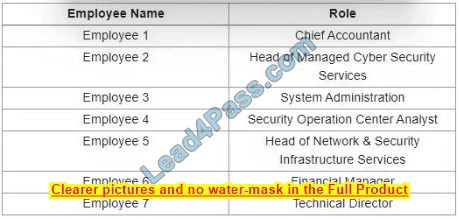
Refer to the exhibit. While developing a Cisco Webex bot, an application reaches the public IP address of the firewall, but traffic is forwarded to the IP address of server 1 instead of the IP address of server 2. What causes this issue?
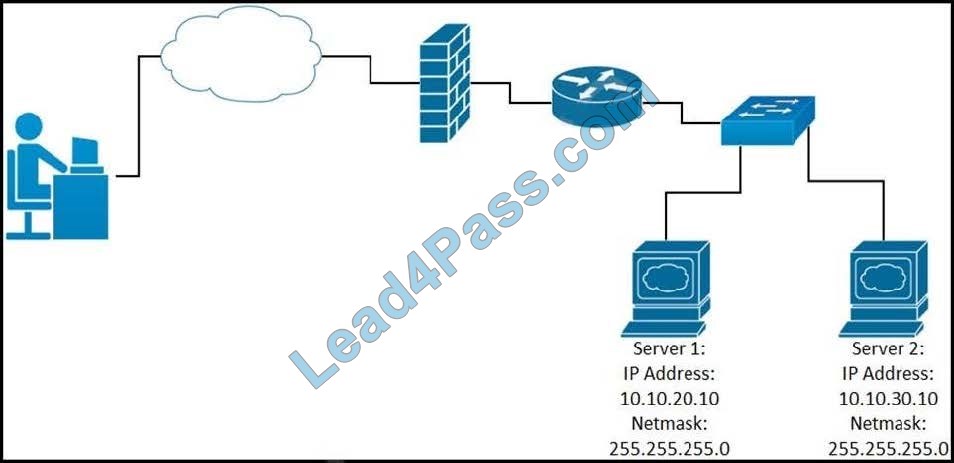
A. The proxy server that rewrites traffic is misconfigured.
B. The router is sending the traffic to server 1 instead of server 2.
C. The switch is forwarding IP traffic to the wrong VLAN.
D. NAT is misconfigured on the firewall.
Correct Answer: D
New Question 4:
Refer to the exhibit.

A network engineer must collect information from the network. The engineer prepares a script to automate workflow by using Cisco Meraki API.
The script must run over nested loops to collect organization and network information and uses the collected data for final collection.
Which process is being automated by using the Python script?
A. Gather the IDs of the ACME organization, the BLDG21 network, and the dents on the network
B. Provide the BLDG21 network information if it is part of the ACME organization
C. Collect the IDs of the clients on the BLDG21 network
D. List the IDs from the ACME organization
Correct Answer: A
New Question 5:
What are the two principles of infrastructure as a code environment? (Choose two.)
A. Components are coupled, and definitions must be deployed for the environment to function.
B. Redeployments cause varying environmental definitions.
C. Environments must be provisioned consistently using the same inputs.
D. Service overlap is encouraged to cater to unique environmental needs.
E. Complete complex systems must be able to be built from reusable infrastructure definitions.
Correct Answer: AC
New Question 6:
Which API is used to obtain data about voicemail ports?
A. Webex Teams
B. Cisco Unified Communications Manager
C. Finesse Gadgets
D. Webex Devices
Correct Answer: A
New Question 7:
DRAG DROP Refer to the exhibit.
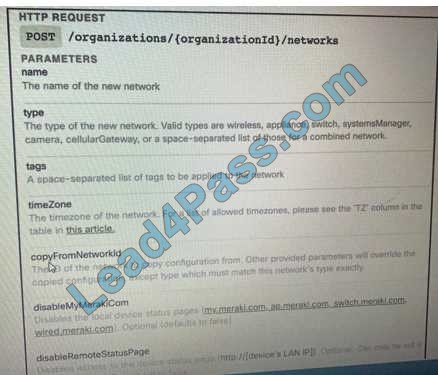
Drag and Drop the code from the bottom onto the box where the code is missing on the Meraki Python script to create a new network.
Select and Place:
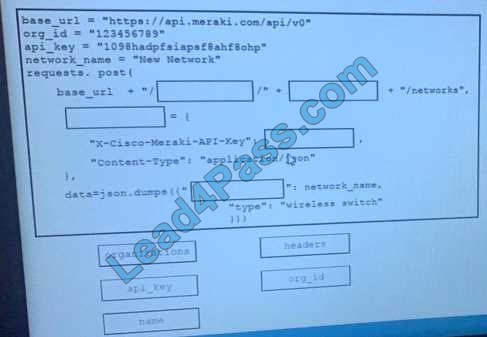
Correct Answer:
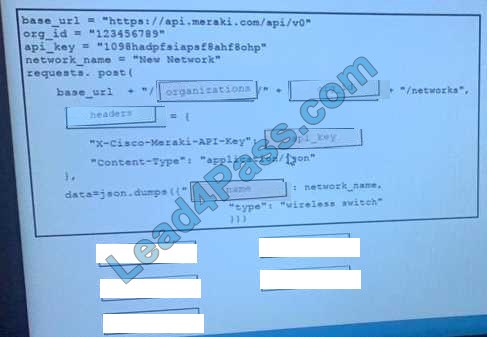
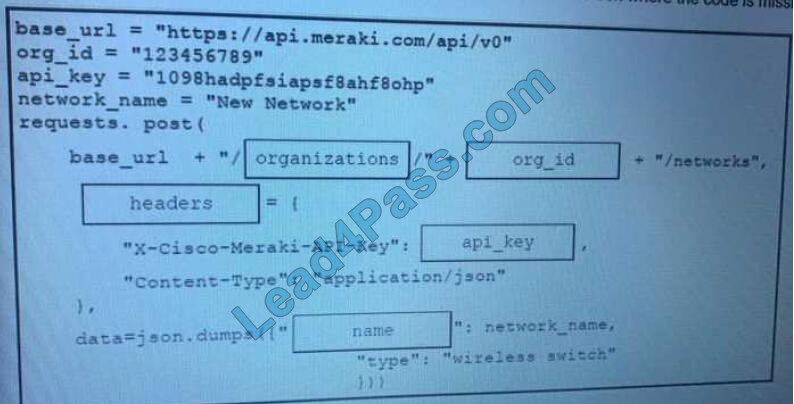
New Question 8:
Access to the management interface of devices must be restricted by using SSH and HTTPS.
Which two ports must be included in the ACLs for the protocols to work? (Choose two.)
A. 22
B. 23
C. 80
D. 443
E. 880
Correct Answer: AD
New Question 9:
What are the two benefits of managing network configuration via APIs? (Choose two.)
A. more security due to locking out manual device configuration
B. configuration on devices becomes less complex
C. eliminates the need for legacy management protocols like SNMP
D. reduction in network changes performed manually
E. increased scalability and consistency of network changes
Correct Answer: DE
New Question 10:
What are two security benefits of a Docker-based application? (Choose two.)
A. natively secures access to secrets that are used by the running application
B. guarantees container images are secured and free of vulnerabilities
C. easier to patch because Docker containers include only dependencies that the application requires
D. prevents information leakage that can occur when unhandled exceptions are returned in HTTP responses
E. allows for the separation of applications that traditionally run on the same host
Correct Answer: AB
…
Latest Complete 294 DevNet Associate 200-901 Certification Exam Questions With Answers Get Lead4Pass 200-901 Exam Dumps: https://www.leads4pass.com/200-901.html (PDF+VCE)
BTW, sharing some more previous free DevNet Associate 200-901 PDFs:
https://drive.google.com/file/d/1nz9bXXwRZmjYcNw5n-BdNgmIOoFoQRVu/
https://drive.google.com/file/d/1AkWXg5-Qk0gvCgce5S3eHXAZg3u5YeOy/
https://drive.google.com/file/d/1hqDUcvc1vHJMiDa15KhDD1Jjp3q8j0hA/