What is CV0-004 exam dumps?
CV0-004 exam dumps meet all preparation requirements for the actual CompTIA Cloud+ exam, providing real-life scenario exam questions and answers.
CompTIA Cloud+ (CV0-004) Verification Candidate:
- Understand cloud architecture and design concepts.
- Implement and maintain a secure cloud environment.
- Successfully provision and configure cloud resources.
- Demonstrate the ability to manage operations throughout the cloud environment life cycle using observability, scaling, and automation.
- Understand fundamental DevOps concepts related to deployment and integration.
- Troubleshoot common issues related to cloud management.
Use CV0-004 exam dump, which contains 285 latest exam questions and answers, accurately hits all core exam questions, reading list:
| Single & multiple choice | 277 Q&As |
| Hotspot | 2 Q&As |
| Simulation labs | 6 Q&As |
| Update time | Feb 2025 |
The actual CompTIA Cloud+ (CV0-004) exam will change over time. But no matter what happens, Leads4Pass can always provide the latest CV0-004 exam dumps as soon as possible, identify the latest materials, and download the latest materials to help you pass easily.
Next, you can verify a free CV0-004 exam question online.
2025 CV0-004 practice test
| Free Share | History test questions |
| 15 Q&As | Comptia cloud+ |
Question 1:
A cloud engineer wants to replace the current on-premises. unstructured data storage with a solution in the cloud. The new solution needs to be cost-effective and highly scalable. Which of the following types of storage would be best to use?
A. File
B. Block
C. Object
D. SAN
Correct Answer: C
Object storage is ideal for cost-effective and highly scalable unstructured data. It allows for the storage of massive amounts of unstructured data in a flat namespace and is not constrained by the rigid structures of file or block storage. Object
storage is highly durable and designed for high levels of scalability and accessibility.
References: The suitability of object storage for unstructured data and scalability is a part of cloud storage technologies covered in CompTIA Cloud+ materials.
Question 2:
A company needs to deploy its own code directly in the cloud without provisioning additional infrastructure. Which of the following is the best cloud service model for the company to use?
A. PaaS
B. SaaS
C. laaS
D. XaaS
Correct Answer: A
Platform as a Service (PaaS) is the best cloud service model for deploying code directly in the cloud without provisioning additional infrastructure. PaaS provides a platform allowing customers to develop, run, and manage applications without the complexity of building and maintaining the infrastructure.References: The PaaS model and its benefits for application deployment are covered under the Cloud Concepts domain in the CompTIA Cloud+ certification.
Question 3:
Which of the following do developers use to keep track of changes made during software development projects?
A. Code drifting
B. Code control
C. Code testing
D. Code versioning
Correct Answer: D
Developers use code versioning to keep track of changes made during software development projects. It is a system that records changes to a file or set of files over time so that specific versions can be recalled later. References: CompTIA Cloud+ Study Guide (V0-004) – Chapter on Software Development in Cloud Environments
Question 4:
A cloud developer is creating a static website that customers will be accessing globally. Which of the following services will help reduce latency?
A. VPC
B. Application load balancer
C. CDN
D. API gateway
Correct Answer: C
A Content Delivery Network (CDN) is the service that will help reduce latency for a static website accessed globally. CDNs distribute content across multiple geographically dispersed servers, allowing users to connect to a server that is closer to them, thereby reducing the time it takes to load the website.
References: The use of CDNs is a common practice to enhance global access and improve user experience, as covered under Cloud Concepts in the CompTIA Cloud+ certification.
Question 5:
A company has applications that need to remain available in the event of the data center being unavailable. The company\’s cloud architect needs to find a solution to maintain business continuity.
Which of following should the company implement?
A. A DR solution for the application between different data centers
B. An off-site backup solution with a third-party vendor
C. laC techniques to recreate the system at a new provider
D. An HA solution for the application inside the data center
Correct Answer: A
A disaster recovery (DR) solution is a set of policies, procedures, and tools that enable an organization to restore or continue its critical functions in the event of a natural or human-induced disaster. A DR solution for the application between different data centers means that the application is replicated or backed up to another location that is geographically separated from the primary data center. This way, if the primary data center becomes unavailable due to a power outage,
fire, flood, cyberattack, or any other cause, the application can be switched over to the secondary data center and resume its operations with minimal downtime and data loss. This solution ensures business continuity and high availability for the application and its users.
References: CompTIA Cloud+ CV0- 003 Study Guide, Chapter 5: Maintaining a Cloud Environment, page 221-222; Disaster recovery planning guide.
Question 6:
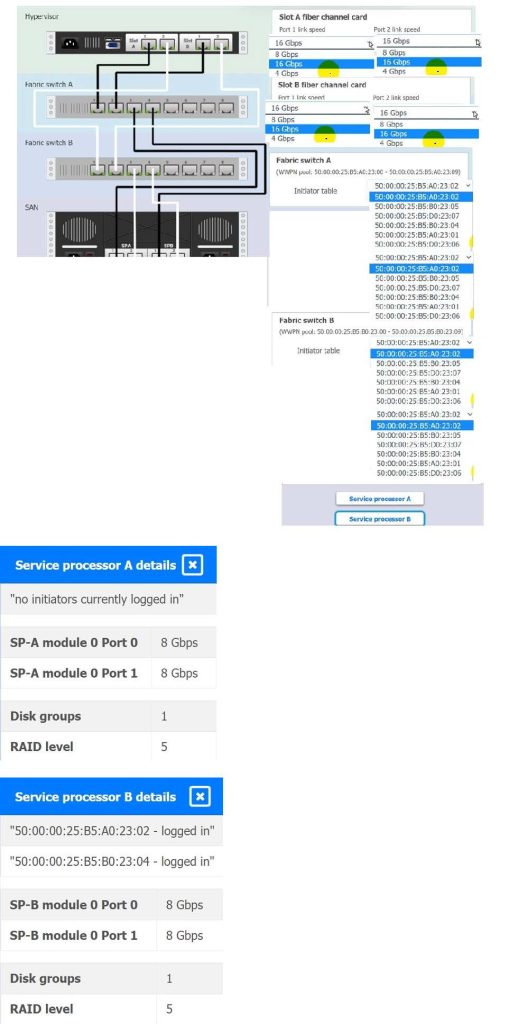
SIMULATION
You are a cloud engineer working for a cloud service provider that is responsible for an IaaS offering.
Your customer, who creates VMs and manages virtual storage, has noticed I/O bandwidth issues and low IOPS (under 9000).
Your manager wants you to verify the proper storage configuration as dictated by your service level agreement (SLA).
The SLA specifies:
1.
Each SFP on the hypervisor host must be set to the maximum link speed allowed by the SAN array. . All SAN array disk groups must be configured in a RAID 5.
2.
The SAN array must be fully configured for redundant fabric paths. . IOPS should not fall below 14000 INSTRUCTIONS Click on each service processor to review the displayed information. Then click on the drop-down menus to change the settings of each device as necessary to conform to the SLA requirements.

A. See the explanation for complete solution.
B. PlaceHolder
C. PlaceHolder
D. PlaceHolder
Correct Answer: A
Based on the SLA requirements and the information provided in the diagram:
For the Hypervisor:
Slot A fiber channel card:
Port 1 link speed should be set to 16 Gbps since it\’s connected to Fabric switch A which supports 16 Gbps.
Port 2 link speed should be set to 8 Gbps because it\’s connected to Fabric switch B which supports up to 8 Gbps.
Slot B fiber channel card:
Port 1 link speed should be set to 16 Gbps since it\’s connected to Fabric switch A which supports 16 Gbps.
Port 2 link speed should be set to 8 Gbps because it\’s connected to Fabric switch B which supports up to 8 Gbps.

Question 7:
An engineer made a change to an application and needs to select a deployment strategy that meets the following requirements:
1.
Is simple and fast
2.
Can be performed on two Identical platforms
Which of the following strategies should the engineer use?
A. Blue-green
B. Canary
C. Rolling
D. in-place
Correct Answer: A
The blue-green deployment strategy is ideal for scenarios where simplicity and speed are crucial. It involves two identical production environments: one (blue) hosts the current application version, while the other (green) is used to deploy the new version. Once testing is completed on the green environment and it\’s ready to go live, traffic is switched from blue to green, ensuring a quick and efficient rollout with minimal downtime.
This method allows for immediate rollback if issues arise, by simply redirecting the traffic back to the blue environment.
References: CompTIA Cloud+ material emphasizes the importance of understanding various cloud deployment strategies, including blue-green, and their application in real-world scenarios to ensure efficient and reliable software deployment in cloud environments.
Question 8:
A company runs a discussion forum that caters to global users. The company\’s monitoring system reports that the home page suddenly is seeing elevated response times, even though internal monitoring has reported no issues or changes. Which of the following is the most likely cause of this issue?
A. Cryptojacking
B. Human error
C. DDoS
D. Phishing
Correct Answer: C
Elevated response times without reported issues or changes internally could indicate a Distributed Denial of Service (DDoS) attack, where multiple systems flood the bandwidth or resources of a targeted system, usually one or more web servers.
References: CompTIA Security+ Guide to Network Security Fundamentals by Mark Ciampa.
Question 9:
An organization has been using an old version of an Apache Log4j software component in its critical software application.
Which of the following should the organization use to calculate the severity of the risk from using this component?
A. CWE
B. CVSS
C. CWSS
D. CVE
Correct Answer: B
The Common Vulnerability Scoring System (CVSS) is what the organization should use to calculate the severity of the risk from using an old version of Apache Log4j software component. CVSS provides an open framework for communicating the characteristics and impacts of IT vulnerabilities.
References: CompTIA Cloud+ Study Guide (V0-004) – Chapter on Risk Management
Question 10:
A critical security patch is required on a network load balancer in a public cloud. The organization has a major sales conference next week, and the Chief Executive Officer does not want any interruptions during the demonstration of an application behind the load balancer.
Which of the following approaches should the cloud security engineer take?
A. Ask the management team to delay the conference.
B. Apply the security patch after the event.
C. Ask the upper management team to approve an emergency patch window.
D. Apply the security patch immediately before the conference.
Correct Answer: C
Given the critical nature of the patch and the upcoming major sales conference, the cloud security engineer should seek approval for an emergency patch window. This approach balances the need for security with the business requirement of no interruptions during the conference.References: The strategy of managing critical updates in alignment with business operations is part of the governance and risk management topics in the CompTIA Cloud+ certification material.
Question 11:
A company that has several branches worldwide needs to facilitate full access to a specific cloud resource to a branch in Spain. Other branches will have only read access. Which of the following is the best way to grant access to the branch in Spain?
A. Set up MFA for the users working at the branch.
B. Create a network security group with required permissions for users in Spain.
C. Apply a rule on the WAF to allow only users in Spain access to the resource.
D. Implement an IPS/IDS to detect unauthorized users.
Correct Answer: B
The best way to grant full access to a specific cloud resource to a branch in Spain, while other branches have only read access, is to create a network security group with the required permissions. This group can be configured to allow full access to users within the branch\’s IP range while restricting others to read-only access.
References:
CompTIA Cloud+ Study Guide (V0-004) – Chapter on Security Configuration
Question 12:
A company wants to move to a multicloud environment and utilize the technology that provides the most portability. Which of the following technology solutions would BEST meet the company\’s needs?
A. Bootstrap
B. Virtual machines
C. Clusters
D. Containers
Correct Answer: D
The technology that provides the most portability for a multicloud environment is containers. Containers are units of software that package an application and its dependencies into a standardized and isolated environment that can run on any platform or cloud service. Containers are lightweight, scalable, and portable, as they do not depend on the underlying infrastructure or operating system.
Containers can also be managed by orchestration tools that automate the deployment, scaling, and networking of containerized applications across multiple clouds.
Reference: [CompTIA Cloud+ Certification Exam Objectives], Domain 1.0 Configuration and Deployment, Objective 1.3 Given a scenario involving integration between multiple cloud environments, select an appropriate solution design.
Question 13:
After accidentally uploading a password for an IAM user in plain text, which of the following should a cloud administrator do FIRST? (Choose two.)
A. Identify the resources that are accessible to the affected IAM user
B. Remove the published plain-text password
C. Notify users that a data breach has occurred
D. Change the affected IAM user\’s password
E. Delete the affected IAM user
Correct Answer: BD
The first step a cloud administrator should take after accidentally uploading a password for an IAM user in plain text is to remove the published plain-text password. This should be done immediately to prevent unauthorized access to the affected user\’s resources. The administrator should then change the password for the affected IAM user to a new, strong password. This will ensure that the user\’s resources are secure and that there is no unauthorized access.
A. Identifying the resources that are accessible to the affected IAM user is important, but it should not be done before removing the plain-text password and changing the password for the affected user. This step can be taken after the immediate security concerns have been addressed.
C. While it is important to notify users of a data breach, this step is not necessary in this situation as the password was accidentally uploaded and there is no evidence that any unauthorized access has occurred. However, the cloud administrator should review their security protocols to ensure that similar incidents do not occur in the future.
E. Deleting the affected IAM user is not necessary in this situation, as the user\’s resources can be secured by changing the password. Deleting the user may cause unnecessary disruption to the user\’s workflow and could result in the loss of important data.
In summary, the first step a cloud administrator should take after accidentally uploading a password for an IAM user in plain text is to remove the published plain-text password, followed by changing the password for the affected user.
Question 14:
An e-commerce store is preparing for an annual holiday sale. Previously, this sale has increased the number of transactions between two and ten times the normal level of transactions. A cloud administrator wants to implement a process to scale the web server seamlessly. The goal is to automate changes only when necessary and with minimal cost.
Which of the following scaling approaches should the administrator use?
A. Scale horizontally with additional web servers to provide redundancy.
B. Allow the load to trigger adjustments to the resources.
C. When traffic increases, adjust the resources using the cloud portal.
D. Schedule the environment to scale resources before the sale begins.
Correct Answer: B
To seamlessly scale the web server for an e-commerce store during an annual sale, it\’s best to allow the load to trigger adjustments to the resources. This approach uses autoscaling to automatically adjust the number of active servers based on the current load, ensuring an automated change that is cost-effective.
References: CompTIA Cloud+ Study Guide (V0-004) – Chapter on Cloud Scalability
Question 15:
A systems administrator has been asked to restore a VM from backup without changing the current VM\’s operating state. Which of the following restoration methods would BEST fit this scenario?
A. Alternate location
B. Rolling
C. Storage live migration
D. In-place
Correct Answer: D
You can also download local study: https://drive.google.com/file/d/1suIRtIw02Nn2uDfi4AxsoEyc0CYZZf1M/ (PDF)
Summarize
Online practice tests help you learn more about the latest exam directions and select complete materials to truly complete your goals.
CV0-004 CompTIA Exam Dumps contains the latest and complete exam questions and answers. Candidates click to download: https://www.leads4pass.com/cv0-004.html, and use the 3-day study plan to help easily complete the goals.
CV0-004 CompTIA Exam Dumps provides two practice methods, PDF and VCE. Learn how to use them through videos.
Finally, best of luck to all!