I checked a lot of information but no more free materials related to the CompTIA CAS-004 Exam in 2024.
Is it because there is no market for CASP+?
Or is everyone no longer willing to share the CASP+ exam?
According to my observation, more people go to landing sale sites to look for free content, and fewer and fewer people blog. Google has lowered the ranking of WordPress blogs, so everyone doesn’t know that there are still many good articles in blogs.

Table of contents:
What is the CASP+ Cybersecurity Exam?
How to pass the CASP+ CAS-004 exam?
CompTIA CAS-004 Exam Requirements
Can I get CompTIA CASP+ without experience?
Can I get CompTIA CASP+ without a degree?
How to Update CompTIA CASP+ 004 Exam Certificate?
What is the CASP+ Cybersecurity Exam?
The CASP+ network security exam is an advanced Network security certificate aimed at enterprise network security and for future security architects and senior security engineers.
There are many such certifications, such as GIAC, CISA, CISSP, CEH, GCIH, etc. It is recommended that you read “Top 10 Most Popular Cybersecurity Certifications“
How to pass the CASP+ CAS-004 exam?
There are many answers to this question. Some people say that to ensure a good mentality, the premise is that you have made the necessary preparations for the exam. My answer is not to magnify those small things too much. What you need to prepare for is to prepare for everything. Get the questions right and enhance your real-world experience through extensive simulation exercises, learn about each question type and answering methods, such as multiple-choice questions, multiple-choice questions, and drag-and-drop activities, as well as the ability to solve problems in a simulated environment.
CompTIA CAS-004 exam questions 2024
| Number of exam questions | Share the number of exam questions online | Material Center | Certification project |
| 600 Q&A | 15 Q&A | Leads4Pass | CompTIA Advanced Security Practitioner |
Question 1:
Due to internal resource constraints, the management team has asked the principal security architect to recommend a solution that shifts partial responsibility for application-level controls to the cloud provider. In the shared responsibility model, which of the following levels of service meets this requirement?
A. laaS
B. SaaS
C. FaaS
D. PaaS
Correct Answer: D
Question 2:
A technician is reviewing the logs and notices a large number of files were transferred to remote sites over three months. This activity then stopped. The files were transferred via TLS-protected HTTP sessions from systems that do not send traffic to those sites.
The technician will define this threat as:
A. a decrypting RSA using obsolete and weakened encryption attack.
B. a zero-day attack.
C. an advanced persistent threat.
D. an on-path attack.
Correct Answer: C
Reference: https://www.internetsociety.org/deploy360/tls/basics/
Question 3:
Before a risk assessment inspection, the Chief Information Officer tasked the systems administrator with analyzing and reporting any configuration issues on the information systems and then verifying existing security settings. Which of the following would be BEST to use?
A. SCAP
B. CVSS
C. XCCDF
D. CMDB
Correct Answer: A
Question 4:
An HVAC contractor requested network connectivity permission to remotely support/troubleshoot equipment issues at a company location. Currently, the company does not have a process that allows vendors remote access to the corporate network.
Which of the following solutions represents the BEST course of action to allow the contractor access?
A. Add the vendor\’s equipment to the existing network Give the vendor access through the standard corporate VPN
B. Give the vendor a standard desktop PC to attach the equipment to Give the vendor access through the standard corporate VPN
C. Establish a certification process for the vendor Allow certified vendors access to the VDI to monitor and maintain the HVAC equipment
D. Create a dedicated segment with no access to the corporate network Implement dedicated VPN hardware for vendor access
Correct Answer: D
Question 5:
SIMULATION
A security engineer needs to review the configurations of several devices on the network to meet the following requirements:
1.
The PostgreSQL server must only allow connectivity in the 10.1.2.0/24 subnet.
2.
The SSH daemon on the database server must be configured to listen to port 4022.
3.
The SSH daemon must only accept connections from a single workstation.
4.
All host-based firewalls must be disabled on all workstations.
5.
All devices must have the latest updates from within the past eight days.
6.
All HDDs must be configured to secure data at rest.
7.
Cleartext services are not allowed.
8.
All devices must be hardened when possible.
INSTRUCTIONS
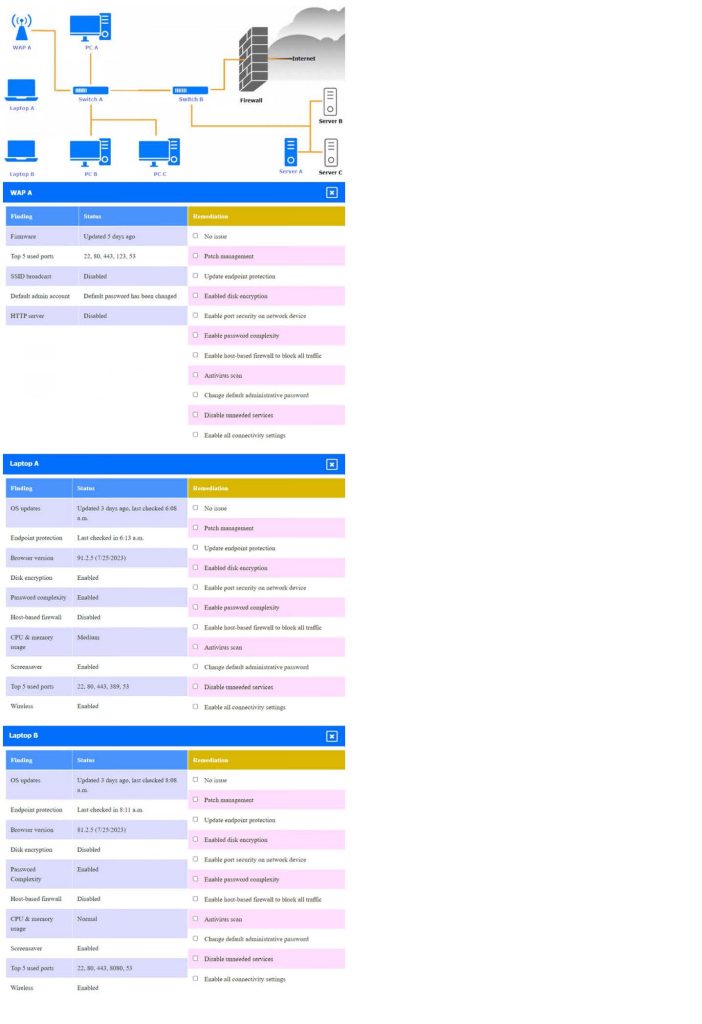
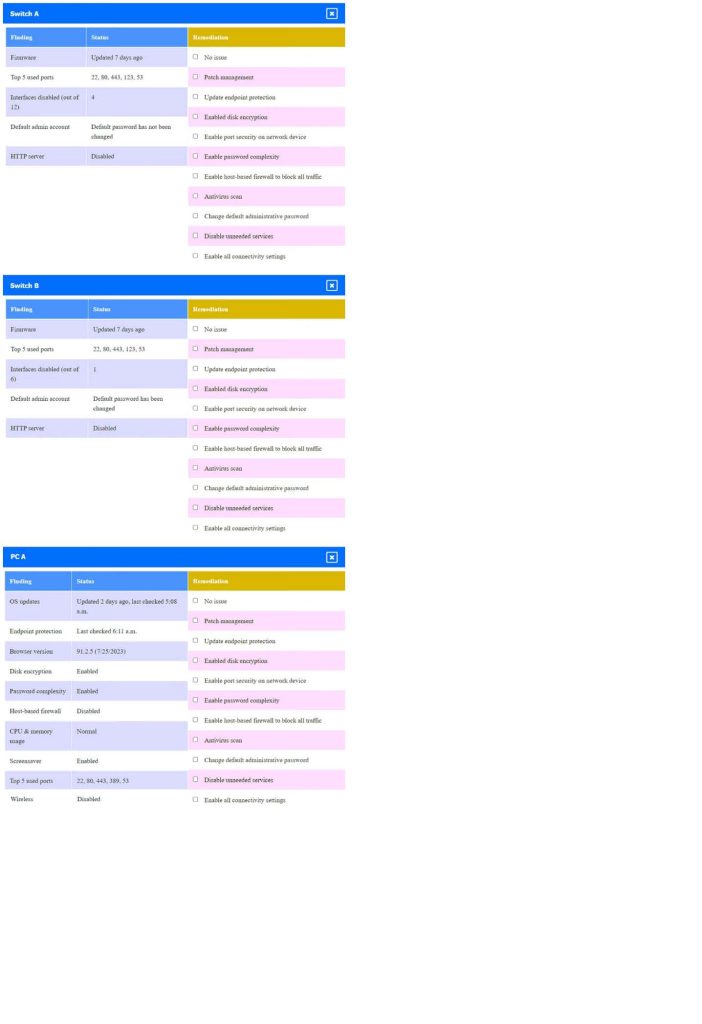
Click on the various workstations and network devices to review the posture assessment results. Remediate any possible issues or indicate that no issue is found.
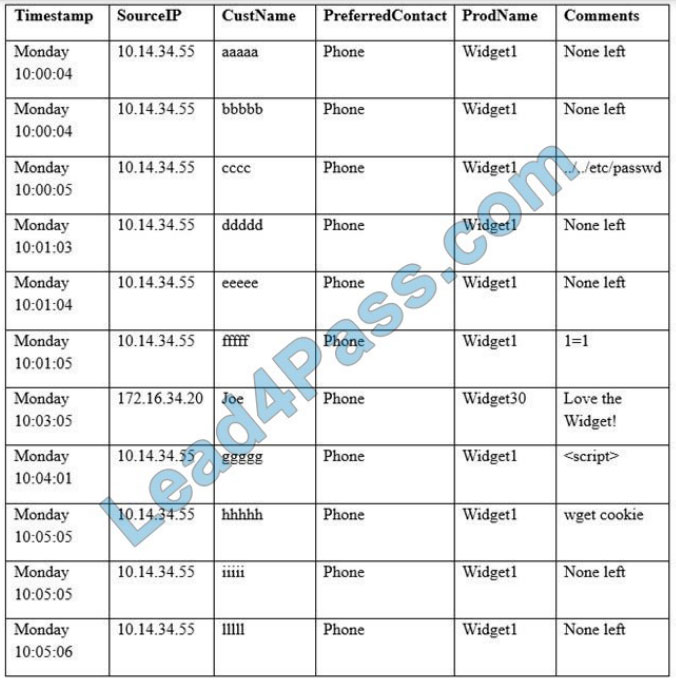
Click on Server A to review output data. Select commands in the appropriate tab to remediate connectivity problems to the PostgreSQL database via SSH.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
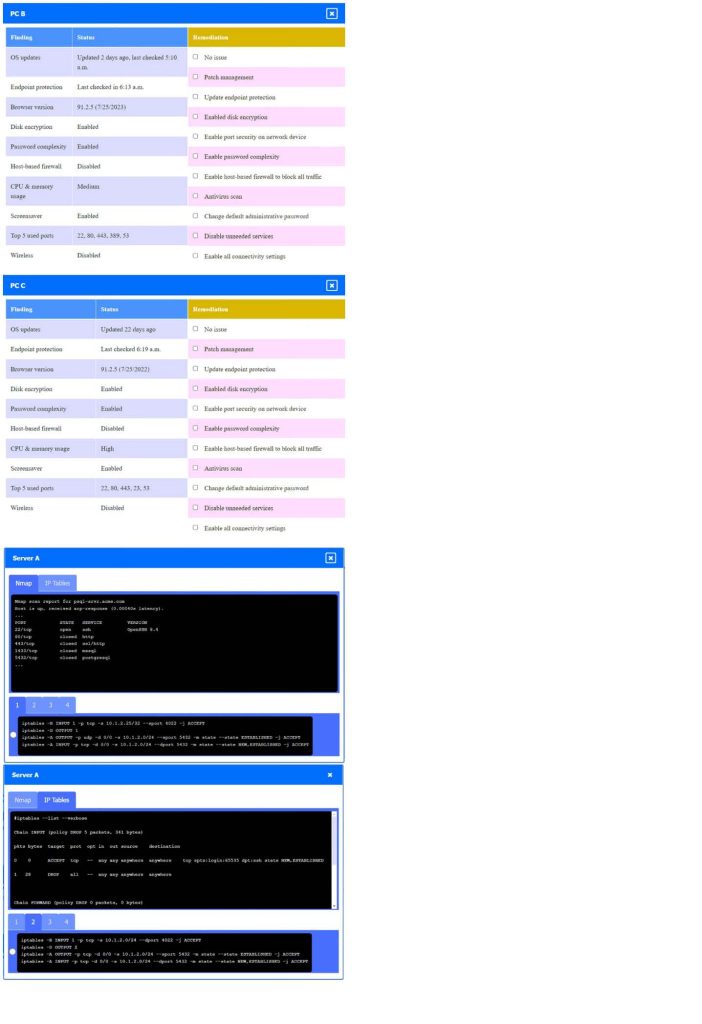
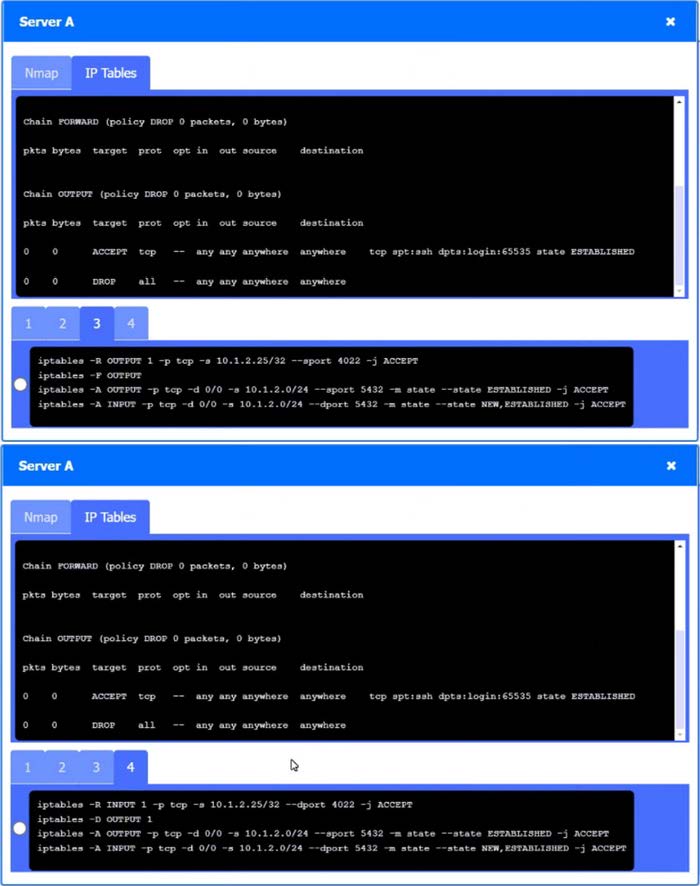
A. Check the answer in the explanation below.
B. PlaceHolder
C. PlaceHolder
D. PlaceHolder
Correct Answer: A

Question 6:
An organization is preparing to migrate its production environment systems from an on-premises environment to a cloud service. The lead security architect is concerned that the organization\’s current methods for addressing risk may not be possible in the cloud environment.
Which of the following BEST describes the reason why traditional methods of addressing risk may not be possible in the cloud?
A. Migrating operations assumes the acceptance of all risks.
B. Cloud providers are unable to avoid risk.
C. Specific risks cannot be transferred to the cloud provider.
D. Risks to data in the cloud cannot be mitigated.
Correct Answer: C
A makes no sense since the CSP isn’t the data owner
B: Cloud providers could avoid the risk via contract
C: Cloud migrations are always a shared risk responsibility but ultimately the data owner/user has the most risk because they have the most to lose.
D: You can mitigate risks with technical and administrative controls in both cloud and on-premises
Question 7:
A financial institution generates a list of newly created accounts and sensitive information daily. The financial institution then sends out a file containing thousands of lines of data. Which of the following would be the best way to reduce the risk of a malicious insider making changes to the file that could go undetected?
A. Write an SIEM rule that generates a critical alert when files are created on the application server.
B. Implement an FIM that automatically generates alerts when the file is accessed by IP addresses that are not associated with the application.
C. Create a script that compares the size of the file on an hourly basis and generates alerts when changes are identified.
D. Tune the rules on the host-based IDS for the application server to trigger automated alerts when the application server is accessed from the internet.
Correct Answer: B
File Integrity Monitoring (FIM) is a technology that can detect changes in files, often used to safeguard critical data. Implementing an FIM solution that generates alerts for access by unauthorized IP addresses would ensure that any unauthorized modifications to the file can be detected and acted upon. This helps in mitigating the risk of insider threats, as it would alert to any changes not made through the expected application process.
Question 8:
A company with multiple locations has taken a cloud-only approach to its infrastructure The company does not have standard vendors or systems resulting in a mix of various solutions put in place by each location The Chief Information Security Officer wants to ensure that the internal security team has visibility into all platforms Which of the following best meets this objective?
A. Security information and event management
B. Cloud security posture management
C. SNMFV2 monitoring and log aggregation
D. Managed detection and response services from a third-party
Correct Answer: A
Security Information and Event Management (SIEM) systems provide real-time analysis of security alerts generated by applications and network hardware. SIEMs are beneficial in environments where there is a mix of various solutions, as they can collect and aggregate logs from multiple sources, providing the internal security team with a centralized view and visibility into all platforms. This would best meet the objective of ensuring visibility into all platforms, regardless of the differing solutions across the company\’s locations.
Question 9:
A security engineer at a company is designing a system to mitigate recent setbacks caused by competitors that are beating the company to market with new products. Several of the products incorporate propriety enhancements developed by the engineer\’s company. The network already includes a SEIM and a NIPS and requires 2FA for all user access. Which of the following systems should the engineer consider NEXT to mitigate the associated risks?
A. DLP
B. Mail gateway
C. Data flow enforcement
D. UTM
Correct Answer: A
Question 10:
A developer needs to implement PKI in an autonomous vehicle\’s software in the most efficient and labor-effective way possible. Which of the following will the developer MOST likely implement?
A. Certificate chain
B. Root CA
C. Certificate pinning
D. CRL
E. OCSP
Correct Answer: B
The developer would most likely implement a Root CA in the autonomous vehicle\’s software. A Root CA is the top-level authority in a PKI that issues and validates certificates for subordinate CAs or end entities. A Root CA can be self-signed
and embedded in the vehicle\’s software, which would reduce the need for external communication and verification. A Root CA would also enable the vehicle to use digital signatures and encryption for secure communication with other vehicles
or infrastructure. Verified References:
https://cse.iitkgp.ac.in/~abhij/publications/PKI++.pdf https://www.digicert.com/blog/connected-cars-need-security-use-pki https://ieeexplore.ieee.org/document/9822667/
Question 11:
An e-commerce company is running a web server on-premises, and the resource utilization is usually less than 30%. During the last two holiday seasons, the server experienced performance issues because of too many connections, and several customers were not able to finalize purchase orders. The company is looking to change the server configuration to avoid this kind of performance issue.
Which of the following is the MOST cost-effective solution?
A. Move the server to a cloud provider.
B. Change the operating system.
C. Buy a new server and create an active-active cluster.
D. Upgrade the server with a new one.
Correct Answer: A
Question 12:
A security architect is implementing a SOAR solution in an organization\’s cloud production environment to support detection capabilities. Which of the following will be the most likely benefit?
A. Improved security operations center performance
B. Automated firewall log collection tasks
C. Optimized cloud resource utilization
D. Increased risk visibility
Correct Answer: A
SOAR solutions (Security Orchestration, Automation, and Response) are designed to help organizations efficiently manage security operations. They can automate the collection and analysis of security data, which improves the performance of a security operations center (SOC) by allowing the security team to focus on more strategic tasks and reduce response times to incidents.
Question 13:
A client is adding scope to a project. Which of the following processes should be used when requesting updates or corrections to the client\’s systems?
A. The implementation engineer requests direct approval from the systems engineer and the Chief Information Security Officer.
B. The change control board must review and approve a submission.
C. The information system security officer provides the systems engineer with the system updates.
D. The security engineer asks the project manager to review the updates for the client\’s system.
Correct Answer: B
Question 14:
Due to internal resource constraints, the management team has asked the principal security architect to recommend a solution that shifts most of the responsibility for application-level controls to the cloud provider. In the shared responsibility model, which of the following levels of service meets this requirement?
A. IaaS
B. SaaS
C. FaaS
D. PaaS
Correct Answer: B
Question 15:
To save time, a company that is developing a new VPN solution has decided to use the OpenSSL library within its proprietary software. Which of the following should the company consider to maximize risk reduction from vulnerabilities introduced by OpenSSL?
A. Include stable, long-term releases of third-party libraries instead of using newer versions.
B. Ensure the third-party library implements the TLS and disable weak ciphers.
C. Compile third-party libraries into the main code statically instead of using dynamic loading.
D. Implement an ongoing, third-party software and library review and regression testing.
Correct Answer: D
…
| 16th to 600th Questions | Free practice method |
| https://www.leads4pass.com/cas-004.html | PDF, VCE, PDF+VCE |
CompTIA CAS-004 Exam Requirements
This is a clear official requirement, and it is also very important to master the exam details:
| Exam code | CAS-004 |
| Exam name | CompTIA Advanced Security Practitioner (CASP+) |
| Length | 165 minutes |
| Questions type | Multiple-choice and performance-based |
| Number of exam questions | Up to 90 |
| Passing score: | Around 80% |
| Equivalent certifications: | Network+, Security+, CySA+, Cloud+, and PenTest+ |
| Languages: | English, Japanese, and Thai |
| Testing provider: | Pearson VUE |
| Testing centers: | Online and in-person |
| Price: | $392 |
Can I get CompTIA CASP+ without experience?
All say CASP+ has at least 10 years of IT management experience, including at least 5 years of practical technical security experience.
I only agree with half of it. First of all, there are no prerequisites for the CASP+ certification exam, which means that your strength determines everything. All the numbers are just a general overview, so if you have the strength to get the certification And if you can prove your strength, then the time and numbers are not important.
Can I get CompTIA CASP+ without a degree?
I said above that there are no prerequisites, anyone can take the CASP+ certification exam, as long as they have the ability.
Let me tell you a joke:
A person applied for a job, and the HR asked if he had any work experience. The applicant said that I had no experience, HR said that we need experienced people, and the applicant said that I don’t have a job, how can I gain experience.
But you can improve your exam experience through simulation exercises, obtain the CASP+ certificate, and then you can tell my jokes to HR.
What can CompTIA CASP+ do?
CASP+ is compliant with ISO 17024 standards and approved by the U.S. Department of Defense (DoD) to meet directive 8140/8570.01-M requirements. The updated CASP+ certification can help certify you in careers such as the following:
- Security Architect
- Security Engineer
- Technical lead analyst
- Application security engineer
Companies like the U.S. Army, Dell, Verizon, and Booz Allen Hamilton all look for CASP+ certification in hiring.
I searched for CASP+ on indeed.com using Los Angeles, CA as an example.
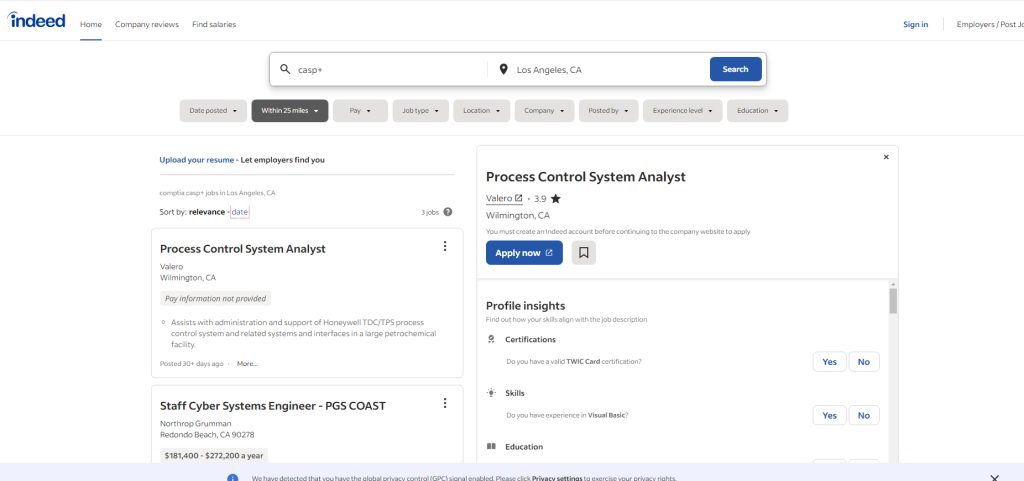

You only need to search according to the region you want and the job position you want to get the precise answer, and you can also know the specific salary.
How to Update CompTIA CASP+ 004 Exam Certificate?
You need to know that the guarantee period of any CompTIA certification is three years. To continue to ensure that the certification is valid, you can participate in the CE (Continuing Education) program to protect your vitality and new opportunities and challenges in this field and provide you with a lot of continuous improvement and development. Good effect. You must know that your CASP+ certification needs to accumulate at least 75 continuing education credits (CEU) within three years and upload it to your certification account to ensure that you automatically renew.