
[How do I get success on the CS0-002 CompTIA CySA+ exam?]
Using the CS0-002 Dumps is the real learning material for you to successfully pass the CompTIA CySA+ exam.CS0-002 dumps have been updated to include 769 real and valid exam practice questions, we confirm that all CS0-002 exam questions have been verified and reviewed to be authentic and valid to ensure you pass the CS0-002 CompTIA CySA+ exam.
Lead4Pass CS0-002 Dumps is responsible for your real goal of successfully passing the CompTIA CySA+ exam. Visit the CS0-002 Dumps: https://www.leads4pass.com/cs0-002.html.
Achieve a successful first attempt to pass the exam.
[Practice Test] CS0-002 Free Dumps Read First
The questions for CS0-002 were last updated on April 24, 2022.
Viewing questions 1-12 out of 769 questions:
QUESTION 1:
A security analyst has received information from a third-party intelligence-sharing resource that indicates employee accounts were breached. Which of the following is the NEXT step the analyst should take to address the issue?
A. Audit access permissions for all employees to ensure the least privilege.
B. Force a password reset for the impacted employees and revoke any tokens.
C. Configure SSO to prevent passwords from going outside the local network.
D. Set up privileged access management to ensure auditing is enabled.
Correct Answer: B
QUESTION 2:
An organization used a third party to conduct a security audit and discovered several deficiencies in the cybersecurity program. The findings noted many external vulnerabilities that were not caught by the vulnerability scanning software, numerous weaknesses that allowed lateral movement, and gaps in monitoring that did not detect the activity of the auditors. Based on these findings, which of the following would be the BEST long-term enhancement to the security program?
A. Quarterly external penetration testing
B. Monthly tabletop scenarios
C. Red-team exercises
D. Audit exercises
Correct Answer: D
QUESTION 3:
A cybersecurity analyst is supporting an incident response effort via threat intelligence. Which of the following is the analyst MOST likely executing?
A. Requirements analysis and collection planning
B. Containment and eradication
C. Recovery and post-incident review
D. Indicator enrichment and research pivoting
Correct Answer: A
QUESTION 4:
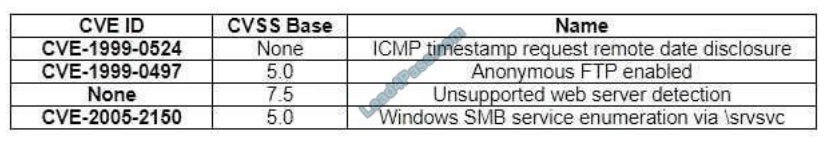
An analyst is participating in the solution analysis process for a cloud-hosted SIEM platform to centralize log monitoring and alerting capabilities in the SOC. Which of the following is the BEST approach for supply chain assessment when selecting a vendor?
A. Gather information from providers, including data center specifications and copies of audit reports.
B. Identify SLA requirements for monitoring and logging.
C. Consult with senior management for recommendations.
D. Perform a proof of concept to identify possible solutions.
Correct Answer: B
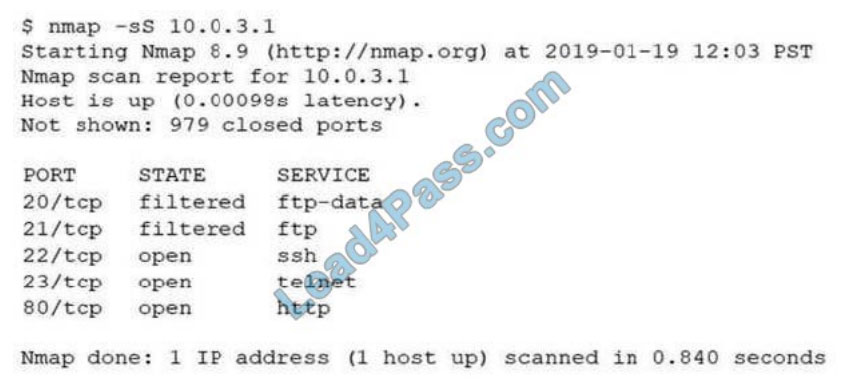
QUESTION 5:
In web application scanning, static analysis refers to scanning:
A. the system for vulnerabilities before installing the application.
B. the compiled code of the application to detect possible issues.
C. an application that is installed and active on a system.
D. an application that is installed on a system that is assigned a static IP.
Correct Answer: A
Reference: https://whatis.techtarget.com/definition/static-analysis-static-code-analysis
QUESTION 6:
During an incident, a cybersecurity analyst found several entries in the web server logs that are related to an IP with a bad reputation. Which of the following would cause the analyst to further review the incident?
A. BadReputationIp – – [2019-04-12 10:43Z] “GET /etc/passwd” 403 1023
B. BadReputationIp – – [2019-04-12 10:43Z] “GET /index.html?src=../.ssh/id_rsa” 401 17044
C. BadReputationIp – – [2019-04-12 10:43Z] “GET /a.php?src=/etc/passwd” 403 11056
D. BadReputationIp – – [2019-04-12 10:43Z] “GET /a.php?src=../../.ssh/id_rsa” 200 15036
E. BadReputationIp – – [2019-04-12 10:43Z] “GET /favicon.ico?src=../usr/share/ icons” 200 19064
Correct Answer: D
QUESTION 7:
A company\’s data is still being exfiltered to business competitors after the implementation of a DLP solution. Which of the following is the most likely reason why the data is still being compromised?
A. Printed reports from the database contain sensitive information
B. DRM must be implemented with the DLP solution
C. Users are not labeling the appropriate data sets
D. DLP solutions are only effective when they are implemented with disk encryption
Correct Answer: B
Reference: https://www.vaultize.com/blog/-enterprise-drm-and-dlp-are-amazing-together.html
QUESTION 8:
A large organization wants to move account registration services to the cloud to benefit from faster processing and elasticity. Which of the following should be done FIRST to determine the potential risk to the organization?
A. Establish a recovery time objective and a recovery point objective for the systems being moved
B. Calculate the resource requirements for moving the systems to the cloud
C. Determine recovery priorities for the assets being moved to the cloud-based systems
D. Identify the business processes that will be migrated and the criticality of each one
E. Perform an inventory of the servers that will be moving and assign priority to each one
Correct Answer: D
QUESTION 9:
Which of the following attacks can be prevented by using output encoding?
A. Server-side request forgery
B. Cross-site scripting
C. SQL injection
D. Command injection
E. Cross-site request forgery
F. Directory traversal
Correct Answer: B
QUESTION 10:
During an investigation, a security analyst determines suspicious activity occurred during the night shift over the weekend. Further investigation reveals the activity was initiated from an internal IP going to an external website. Which of the following would be the MOST appropriate recommendation to prevent the activity from happening in the future?
A. An IPS signature modification for the specific IP addresses
B. An IDS signature modification for the specific IP addresses
C. A firewall rule that will block port 80 traffic
D. A firewall rule that will block traffic from the specific IP addresses
Correct Answer: D
QUESTION 11:
The Chief Information Officer (CIO) for a large manufacturing organization has noticed a significant number of unknown devices with possible malware infections are on the organization\’s corporate network. Which of the following would work BEST to prevent the issue?
A. Reconfigure the NAC solution to prevent access based on a full device profile and ensure antivirus is installed.
B. Segment the network to isolate all systems that contain highly sensitive information, such as intellectual property.
C. Implement certificate validation on the VPN to ensure only employees with the certificate can access the company network.
D. Update the antivirus configuration to enable behavioral and real-time analysis on all systems within the network.
Correct Answer: A
QUESTION 12:
A development team is testing a new application release. The team needs to import existing client PHI data records from the production environment to the test environment to test accuracy and functionality. Which of the following would BEST protect the sensitivity of this data while still allowing the team to perform the testing?
A. Deidentification
B. Encoding
C. Encryption
D. Watermarking
Correct Answer: A
……
[Google Drive] CS0-002 Free Dumps Online Download:https://drive.google.com/file/d/1bsSyU7x5kxHDZv6gKqUgh6IMMz_B75ZS/view?usp=sharing
[Why Choose Lead4Pass CS0-002 Dumps?]
Lead4Pass CS0-002 Dumps comes with both PDF and VCE study tools to help you study easily and quickly pass the CompTIA CySA+ exam in a variety of environments.769 complete CS0-002 dumps questions can be obtained at the address: https://www.leads4pass.com/cs0-002.html. Congratulations in advance on your success.




![[2021.3] lead4pass cs0-002 practice test q4](https://www.braindump4it.com/wp-content/uploads/2021/03/q4.jpg)
![[2021.3] lead4pass cs0-002 practice test q5](https://www.braindump4it.com/wp-content/uploads/2021/03/q5.jpg)