New updated CompTIA CS0-002 exam questions from Lead4Pass CompTIA CS0-002 dumps!
Welcome to download the latest Lead4Pass CompTIA CS0-002 dumps with PDF and VCE: https://www.leads4pass.com/cs0-002.html (260 Q&As)
[CompTIA CS0-002 exam pdf] CompTIA CS0-002 exam PDF uploaded from google drive, online download provided by the latest update of Lead4pass:
https://drive.google.com/file/d/1c4cmZiff661oldNP09QBlTZMvUEPe755/
Latest update CompTIA CS0-002 exam questions and answers online practice test
QUESTION 1
An information security analyst is working with a data owner to identify the appropriate controls to preserve the
confidentiality of data within an enterprise environment One of the primary concerns is the exfiltration of data by malicious
insiders, Which of the following controls is the MOST appropriate to mitigate risks?
A. Data deduplication
B. OS fingerprinting
C. Digital watermarking
D. Data loss prevention
Correct Answer: D
QUESTION 2
A company\\’s modem response team is handling a threat that was identified on the network Security analysts have as
at remote sites. Which of the following is the MOST appropriate next step in the incident response plan?
A. Quarantine the webserver
B. Deploy virtual firewalls
C. Capture a forensic image of the memory and disk
D. Enable webserver containerization
Correct Answer: B
QUESTION 3
A security analyst, who is working for a company that utilizes Linux servers, receives the following results from a
vulnerability scan: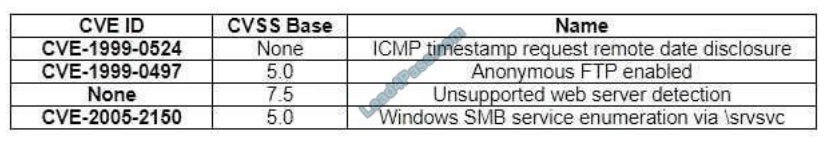
Which of the following is MOST likely a false positive?
A. ICMP timestamp request remote data disclosure
B. Windows SMB service enumeration via \srvsvc
C. Anonymous FTP enabled
D. Unsupported web server detection
Correct Answer: B
QUESTION 4
An analyst performs a routine scan of a host using Nmap and receives the following output: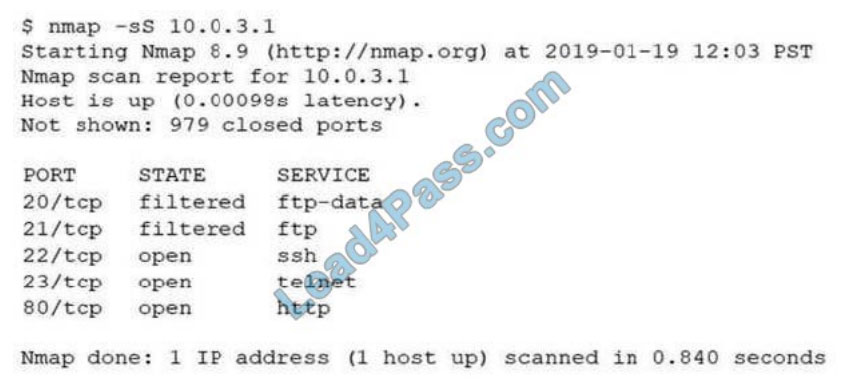
Which of the following should the analyst investigate FIRST?
A. Port 21
B. Port 22
C. Port 23
D. Port 80
Correct Answer: C
QUESTION 5
A Chief Information Security Officer (CISO) is concerned the development team, which consists of contractors, has too
much access to customer data
Developers use personal workstations, giving the company little to no visibility into the development activities.
Which of the following would be BEST to implement to alleviate the CISO\\’s concern?
A. DLP
B. Encryption
C. Test data
D. NDA
Correct Answer: D
QUESTION 6
A security analyst received an alert from the SIEM indicating numerous login attempts from users outside their usual
geographic zones, all of which were initiated through the web-based mail server. The logs indicate all domain accounts
experienced two login attempts during the same time frame. Which of the following is the MOST likely cause of this
issue?
A. A password-spraying attack was performed against the organization.
B. A DDoS attack was performed against the organization.
C. This was normal shift work activity; the SIEM\\’s AI is learning.
D. A credentialed external vulnerability scan was performed.
Correct Answer: A
Reference: https://doubleoctopus.com/security-wiki/threats-and-tools/password-spraying/
QUESTION 7
Which of the following attacks can be prevented by using output encoding?
A. Server-side request forgery
B. Cross-site scripting
C. SQL injection
D. Command injection
E. Cross-site request forgery
F. Directory traversal
Correct Answer: B
QUESTION 8
A small electronics company decides to use a contractor to assist with the development of a new FPGA- based device.
Several of the development phases will occur off-site at the contractor\\’s labs. Which of the following is the main
concern a security analyst should have with this arrangement?
A. Making multiple trips between development sites increases the chance of physical damage to the FPGAs.
Latest CS0-002 Dumps | CS0-002 PDF Dumps | CS0-002 VCE Dumps 4 / 7
https://www.leads4pass.com/CS0-002.html
2021 Latest lead4pass CS0-002 PDF and VCE dumps Download
B. Moving the FPGAs between development sites will lessen the time that is available for security testing.
C. Development phases occurring at multiple sites may produce change management issues.
D. FPGA applications are easily cloned, increasing the possibility of intellectual property theft.
Correct Answer: B
Reference: https://www.eetimes.com/how-to-protect-intellectual-property-in-fpgas-devices-part-1/#
QUESTION 9
Employees of a large financial company are continuously being Infected by strands of malware that are not detected by
EDR tools. When of the following Is the BEST security control to implement to reduce corporate risk while allowing
employees to exchange files at client sites?
A. MFA on the workstations
B. Additional host firewall rules
C. VDI environment
D. Hard drive encryption
E. Network access control
F. Network segmentation
Correct Answer: B
QUESTION 10
Which of the following technologies can be used to house the entropy keys for task encryption on desktops and
laptops?
A. Self-encrypting drive
B. Bus encryption
C. TPM D. HSM
Correct Answer: A
QUESTION 11
An organization needs to limit its exposure to accidental disclosure when employees send emails that contain personal
information to recipients outside the company Which of the following technical controls would BEST accomplish this
goal?
A. DLP
B. Encryption
C. Data masking
D. SPF
Correct Answer: A
QUESTION 12
A security analyst suspects a malware infection was caused by a user who downloaded malware after clicking
http:///a.php is a phishing email.
To prevent other computers from being infected by the same malware variation, the analyst should create a rule on the
__________.
A. email server that automatically deletes attached executables.
B. IDS to match the malware sample.
C. proxy to block all connections to.
D. firewall to block connection attempts to dynamic DNS hosts.
Correct Answer: C
QUESTION 13
As part of a review of incident response plans, which of the following is MOST important for an organization to
understand when establishing the breach notification period?
A. Organizational policies
B. Vendor requirements and contracts
C. Service-level agreements
D. Legal requirements
Correct Answer: D
The above content: shared CS0-002 exam pdf, CS0-002 Exam Questions And Answers, CS0-002 exam video, and get the complete CS0-002 exam dump path.
For information about CS0-002 Dumps from Lead4pass (including PDF and VCE), please visit: https://www.leads4pass.com/cs0-002.html (260 Q&A)
ps.
Get free CompTIA CS0-002 dumps PDF online: https://drive.google.com/file/d/1c4cmZiff661oldNP09QBlTZMvUEPe755/