
CompTIA sy0-601 exam is a newly launched CompTIA Security+ exam in 2020-2021.
The exam verifies whether successful candidates have the knowledge and skills required to assess the security status of the enterprise environment and recommend and implement appropriate security solutions;
monitor and protect hybrid environments, including cloud, mobile, and the Internet of Things; and understand applicable laws and policies. Operating under circumstances, including governance, risk, and compliance principles; identifying, analyzing, and responding to security incidents and accidents.
On this site, we will help you first try the exam test to verify your current strength! And we will also share the PDF mode for you to download and study, not only that, but we also provide complete CompTIA SY0-601 exam questions and answers https://www.leads4pass.com/sy0-601.html. The complete exam questions are verified by CompTIA Security+ experts to ensure that all exam questions and answers are valid. Next, I will share some exam details tips and exam practice questions.
Tips: First of all, you need to know the time to participate in the exam, the number of questions, the type of questions, the time of the exam, the passing score, the price, etc. These can all be viewed through the official website.
Click here to view the specific information.
CompTIA sy0-601 free exam PDF download online
Google Drive: https://drive.google.com/file/d/1UGIiWRMaMCKbj5oE9zch0yZwX-Hk8zsv/view?usp=sharing
CompTIA sy0-601 exam practice test
All answers are announced at the end of the article
QUESTION 1
A cybersecurity department purchased o new PAM solution. The team is planning to randomize the service account
credentials of the Windows server first. Which of the following would be the BEST method to increase the security on
the Linux server?
A. Randomize the shared credentials
B. Use only guest accounts to connect.
C. Use SSH keys and remove generic passwords
D. Remove all user accounts.
QUESTION 2
A security analyst has been asked to investigate a situation after the SOC started to receive alerts from the SIEM. The
analyst first looks at the domain controller and finds the following events:
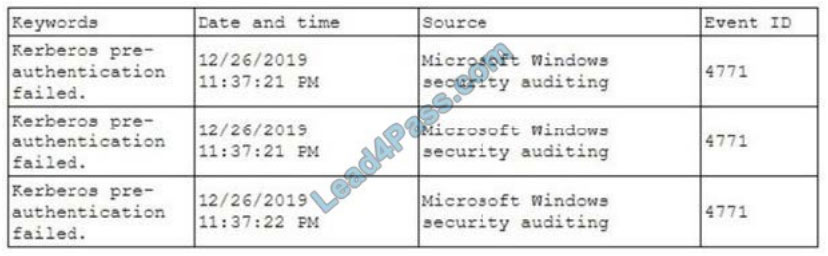
To better understand what is going on, the analyst runs a command and receives the following output:
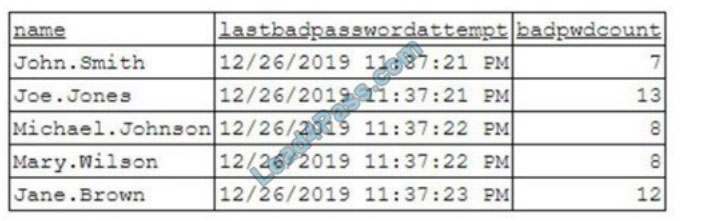
Based on the analyst\\’s findings, which of the following attacks is being executed?
A. Credential harvesting
B. Keylogger
C. Brute-force
D. Spraying
QUESTION 3
In the middle of a cybersecurity, a security engineer removes the infected devices from the network and lock down all
compromised accounts. In which of the following incident response phases is the security engineer currently operating?
A. Identification
B. Preparation
C. Eradiction
D. Recovery
E. Containment
QUESTION 4
A security administrator suspects there may be unnecessary services running on a server. Which of the following tools
will the administrator MOST likely use to confirm the suspicions?
A. Nmap
B. Wireshark
C. Autopsy
D. DNSEnum
QUESTION 5
A network engineer has been asked to investigate why several wireless barcode scanners and wireless computers in a
warehouse have intermittent connectivity to the shipping server. The barcode scanners and computers are all on forklift trucks and move around the warehouse during their regular use. Which of the following should the engineer do to determine the issue? (Choose two.)
A. Perform a site survey
B. Deploy an FTK Imager
C. Create a heat map
D. Scan for rogue access points
E. Upgrade the security protocols
F. Install a captive portal
QUESTION 6
A security analyst notices several attacks are being blocked by the NIPS but does not see anything on the boundary
firewall logs. The attack seems to have been thwarted Which of the following resiliency techniques was applied to the
network to prevent this attack?
A. NIC Teaming
B. Port mirroring
C. Defense in depth
D. High availability
E. Geographic dispersal
QUESTION 7
Which of the following incident response steps involves actions to protect critical systems while maintaining business
operations?
A. Investigation
B. Containment
C. Recovery
D. Lessons learned
QUESTION 8
To secure an application after a large data breach, an e-commerce site will be resetting all users\\’ credentials. Which of
the following will BEST ensure the site\\’s users are not compromised after the reset?
A. A password reuse policy
B. Account lockout after three failed attempts
C. Encrypted credentials in transit
D. A geofencing policy based on login history
QUESTION 9
Which of the following organizational policies are MOST likely to detect fraud that is being conducted by existing
employees? (Select TWO).
A. Offboarding
B. Mandatory vacation
C. Job rotation
D. Background checks
E. Separation of duties
F. Acceptable use
QUESTION 10
An analyst is trying to identify insecure services that are running on the internal network After performing a port scan the analyst identifies that a server has some insecure services enabled on default ports Which of the following BEST
describes the services that are currently running and the secure alternatives for replacing them\\’ (Select THREE)
A. SFTP FTPS
B. SNMPv2 SNMPv3
C. HTTP, HTTPS
D. TFTP FTP
E. SNMPv1, SNMPv2
F. Telnet SSH
G. TLS, SSL
H. POP, IMAP
I. Login, rlogin
QUESTION 11
A public relations team will be taking a group of guest on a tour through the facility of a large e-commerce company. The day before the tour, the company sends out an email to employees to ensure all whiteboars are cleaned and all desks are cleared. The company is MOST likely trying to protect against.
A. Loss of proprietary information
B. Damage to the company\\’s reputation
C. Social engineering
D. Credential exposure
QUESTION 12
Which of the following types of controls is a turnstile?
A. Physical
B. Detective
C. Corrective
D. Technical
QUESTION 13
A security analyst sees the following log output while reviewing web logs:

Which of the following mitigation strategies would be BEST to prevent this attack from being successful?
A. Secure cookies
B. Input validation
C. Code signing
D. Stored procedures
Publish the answer
| Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 |
| C | D | E | A | AC | C | B | C | BC | BCF | C | A | B |
CompTIA sy0-601 free exam PDF download online
Google Drive: https://drive.google.com/file/d/1UGIiWRMaMCKbj5oE9zch0yZwX-Hk8zsv/view?usp=sharing
This article shares the latest updated CompTIA SY0-601 exam dump, exam practice questions and exam PDF, and exam tips. These can help you understand your current strength and promote your progress!
Lead4Pass sy0-601 complete exam questions are verified by our CompTIA Security+ experts as a valid exam dump https://www.leads4pass.com/sy0-601.html. It can help you pass the exam successfully for the first time!
Braindump4it shares CompTIA exam questions and answers for free throughout the year. If you like, please bookmark and share! Thanks!