Whether you are a novice or an exam candidate, you can use this article as your learning object, I will share the most popular online complete knowledge and learning materials.
With the advancement of society, the online world has become more and more complex, various network security problems have arisen, and the opportunities for bad actors to steal, damage or destroy are also increasing. The increase in cybercrime is driving the demand for cybersecurity professionals.
The job outlook for studying cybersecurity has grown accordingly.
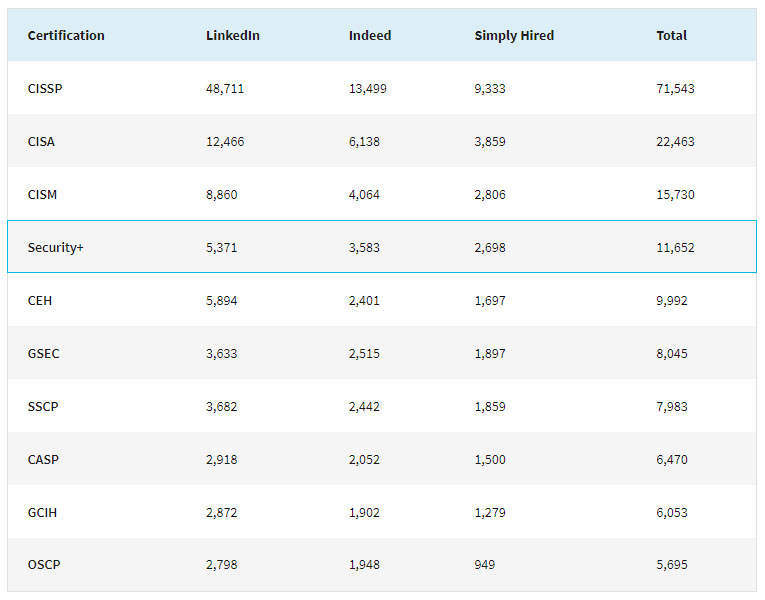
Do you know that there is a lot of network security knowledge in this world, if you are a novice, you will be confused about how to choose. Below I will share a picture of the most popular network security certification in the world, if you don’t know how to do it, then choose the most popular, This is definitely not wrong.
The following table shows more than 300 different cybersecurity certifications searched on three popular recruiting sites, LinkedIn, Indeed, and Simply Hired, and these 10 certifications appear the most in total U.S. job listings (The data is from last year and is for reference only.)
1.Certified Information Systems Security Professional (CISSP)
Earning a CISSP demonstrates your ability to effectively design, implement, and manage a best-in-class cybersecurity program.
https://www.isc2.org/Certifications/CISSP
Provide learning materials:
CISSP practice test:examfast.com
PDF + VCE download: https://www.leads4pass.com/
2. Certified Information Systems Auditor (CISA)
Prove your expertise in IS/IT auditing, controls and security and rank among the most qualified in the industry.
https://www.isaca.org/credentialing/cisa
Provide learning materials:
CISA practice test: examfast.com
PDF + VCE download: https://www.leads4pass.com/
3. Certified Information Security Manager (CISM)
ISACA Certified Information Security Manager (CISM) certification demonstrates expertise in information security governance, project development and management, incident management, and risk management.
CISM work practices are valid until 31 May 2022
Updated CISM exam content syllabus effective from 1 June 2022
https://www.isaca.org/credentialing/cism
Provide learning materials:
CISM practice test: micvce.com
PDF + VCE download: https://www.leads4pass.com/
4. Security+
CompTIA Security+ is a global certification that validates the essential skills required to perform core security functions and pursue a career in IT security.
https://www.comptia.org/certifications/security
Provide learning materials:
Security+ practice test: braindump4it.com
PDF + VCE download: https://www.leads4pass.com/
5. Certified Ethical Hacker (CEH)
Certified Ethical Hacker CEH v11 will teach you the latest commercial-grade hacking tools, techniques, and methods that hackers and information security professionals use to break into organizations legally.
https://www.eccouncil.org/programs/certified-ethical-hacker-ceh/
Provide learning materials:
CEH practice test: latestvce.com
PDF + VCE download: https://www.leads4pass.com/
6. GIAC Security Essentials Certification (GSEC)
The GIAC Security Fundamentals (GSEC) certification validates a practitioner’s knowledge of information security, not just simple terms and concepts.
https://www.giac.org/certifications/security-essentials-gsec/
Provide learning materials:
GSEC practice test: no
PDF + VCE download: no
7.Systems Security Certified Practitioner (SSCP)
Implement, monitor and manage IT infrastructure using security best practices, policies and procedures developed by (ISC)²’s cybersecurity experts.
https://www.isc2.org/Certifications/SSCP
Provide learning materials:
SSCP practice test: no
PDF download: https://drive.google.com/file/d/1-HW8f-R1b2-m5l99Y8mUD0U1bP-S_TAE/view?usp=sharing
PDF + VCE download: https://www.leads4pass.com/
8. CompTIA Advanced Security Practitioner (CASP+)
CompTIA Advanced Security Practitioner (CASP+) is an advanced cybersecurity certification for security architects and senior security engineers responsible for leading and improving enterprise cybersecurity readiness.
https://www.comptia.org/certifications/comptia-advanced-security-practitioner
Provide learning materials:
CASP+ practice test: braindump4it.com
PDF + VCE download: https://www.leads4pass.com/
9. GIAC Certified Incident Handler (GCIH)
The GIAC Incident Handler certification verifies a practitioner’s ability to detect, respond to, and resolve computer security incidents using a broad range of fundamental security skills.
https://www.giac.org/certifications/certified-incident-handler-gcih/
Provide learning materials:
GCIH practice test: no
PDF Download: https://drive.google.com/file/d/1sBIEb96vghkRmlbD-gLhjigSAw9dHiAi/view?usp=sharing
PDF + VCE download: no
10. Offensive Security Certified Professional (OSCP)
Offensive Security’s OSCP has become one of the most sought-after certifications for penetration testers. This exam tests your ability to compromise a range of targeted computers using multiple exploitation steps and generates a detailed penetration test report for each attack.
https://www.offensive-security.com/pwk-oscp/
Provide learning materials:
OSCP practice test: no
PDF + VCE download: no
PDF + VCE download: no
Is Cybersecurity Certification Worth It?
A survey by (ISC)² found that 70% of cybersecurity professionals surveyed in the U.S. require employer certification.
According to the same study, security certifications can also lead to big pay raises. The right credentials can also make you more attractive to recruiters and hiring managers alike.
P.s. Latest Updated CompTIA Security+ 2022 Exam Questions and Answers
QUESTION 1:
A company\’s Chief Information Security Officer (CISO) recently warned the security manager that the company\’s Chief Executive Officer (CEO) is planning to publish a controversial option article in a national newspaper, which may result in new cyberattacks Which of the following would be BEST for the security manager to use in a threat mode?
A. Hacktivists
B. White-hat hackers
C. Script kiddies
D. Insider threats
Correct Answer: A
Hacktivists – “a person who gains unauthorized access to computer files or networks in order to further social or political ends.”
QUESTION 2:
A security analyst reviews the datacenter access logs for a fingerprint scanner and notices an abundance of errors that correlate with users\’ reports of issues accessing the facility. Which of the following MOST likely the cause of the cause of the access issues?
A. False rejection
B. Cross-over error rate
C. Efficacy rale
D. Attestation
Correct Answer: A
where a legitimate user is not recognized. This is also referred to as a Type I error or false non-match rate (FNMR). FRR is measured as a percentage.
QUESTION 3:
A security analyst notices several attacks are being blocked by the NIPS but does not see anything on the boundary firewall logs. The attack seems to have been thwarted Which of the following resiliency techniques was applied to the network to prevent this attack?
A. NIC Teaming
B. Port mirroring
C. Defense in depth
D. High availability
E. Geographic dispersal
Correct Answer: C
QUESTION 4:
An organization suffered an outage and a critical system took 90 minutes to come back online. Though there was no data loss during the outage, the expectation was that the critical system would be available again within 60 minutes.
Which of the following is the 60- minute expectation an example of:
A. MTBF
B. RPO
C. MTTR
D. RTO
Correct Answer: D
https://www.enterprisestorageforum.com/management/rpo-and-rto-understanding-the-differences/
QUESTION 5:
A backdoor was detected on the containerized application environment. The investigation detected that a zero-day vulnerability was introduced when the latest container image version was downloaded from a public registry. Which of the following is the BEST solution to prevent this type of incident from occurring again?
A. Deploy an IPS solution capable of detecting signatures of attacks targeting containers
B. Define a vulnerability scan to assess container images before being introduced on the environment
C. Create a dedicated VPC for the containerized environment
Correct Answer: A
QUESTION 6:
Which of the following describes the BEST approach for deploying application patches?
A. Apply the patches to systems in a testing environment then to systems in a staging environment, and finally to production systems.
B. Test the patches in a staging environment, develop against them in the development environment, and then apply them to the production systems
C. Test the patches m a test environment apply them to the production systems and then apply them to a staging environment
D. Apply the patches to the production systems apply them in a staging environment, and then test all of them in a testing environment
Correct Answer: A
QUESTION 7:
A security engineer has enabled two-factor authentication on all workstations. Which of the following approaches are the MOST secure? (Select TWO).
A. Password and security question
B. Password and CAPTCHA
C. Password and smart card
D. Password and fingerprint
E. Password and one-time token
F. Password and voice
Correct Answer: CD
QUESTION 8:
A security assessment found that several embedded systems are running unsecure protocols. These Systems were purchased two years ago and the company that developed them is no longer in business Which of the following constraints BEST describes the reason the findings cannot be remediated?
A. inability to authenticate
B. Implied trust
C. Lack of computing power
D. Unavailable patch
Correct Answer: D
QUESTION 9:
A company was compromised, and a security analyst discovered the attacker was able to get access to a service account. The following logs were discovered during the investigation:

Which of the following MOST likely would have prevented the attacker from learning the service account name?
A. Race condition testing
B. Proper error handling
C. Forward web server logs to a SIEM
D. Input sanitization
Correct Answer: B
QUESTION 10:
A security analyst is reviewing the following command-line output: Which of the following Is the analyst observing?

A. IGMP spoofing
B. URL redirection
C. MAC address cloning
D. DNS poisoning
Correct Answer: C
QUESTION 11:
To further secure a company\’s email system, an administrator is adding public keys to DNS records in the company\’s domain Which of the following is being used?
A. PFS
B. SPF
C. DMARC
D. DNSSEC
Correct Answer: D
QUESTION 12:
Which of the following would be the BEST method for creating a detailed diagram of wireless access points and hot-spots?
A. Footprinting
B. White-box testing
C. A drone/UAV
D. Pivoting
Correct Answer: A
QUESTION 13:
After a WiFi scan of a local office was conducted, an unknown wireless signal was identified Upon investigation, an unknown Raspberry Pi device was found connected to an Ethernet port using a single connection. Which of the following BEST describes the purpose of this device?
A. Evil twin
B. Rogue access point
C. On-path attack
Correct Answer: B
……
CompTIA Security+ 2022 Exam Questions and Answers Online Download: https://drive.google.com/file/d/1lJ911sJMs1cOPYD3MCKznr89c5s5KTn5/view?usp=sharing
View 572 Exam Questions And Answers

