
Where can I get the real (CASP) CAS-003 exam questions? Braindump4it shares the latest and effective CompTIA CASP CAS-003 exam questions and answers, online practice tests, and the most authoritative CompTIA exam experts update CAS-003 exam questions throughout the year. Get the full CAS-003 exam dumps selection: https://www.leads4pass.com/cas-003.html (491 Q&As). Pass the exam with ease!
Table of Contents:
- Latest CompTIA CASP CAS-003 google drive
- Effective CompTIA CAS-003 exam practice questions
- Related CAS-003 Popular Exam resources
- Lead4Pass Year-round Discount Code
- What are the advantages of Lead4pass?
Latest CompTIA CAS-003 google drive
[PDF] Free CompTIA CAS-003 pdf dumps download from Google Drive: https://drive.google.com/open?id=1QZw_MPIYiI6w1CWtMK7AYYZcaO4XT6KY
CompTIA Advanced Security Practitioner (CASP+):https://www.comptia.org/certifications/comptia-advanced-security-practitioner
About the Exam
The CASP+ certification validates advanced-level competency in risk management, enterprise security operations and architecture, research and collaboration, and integration of enterprise security. The CASP+ exam covers the following:
- Enterprise security domain expanded to include operations and architecture concepts, techniques and requirements
- More emphasis on analyzing risk through interpreting trend data and anticipating cyberdefense needs to meet business goals
- Expanding security control topics to include mobile and small-form-factor devices, as well as software vulnerability
- Broader coverage of integrating cloud and virtualization technologies into a secure enterprise architecture
- Inclusion of implementing cryptographic techniques, such as blockchain, cryptocurrency and mobile device encryption
Latest updates CompTIA CAS-003 exam practice questions
QUESTION 1
A security consultant is evaluating forms which will be used on a company website. Which of the following techniques or
terms is MOST effective at preventing malicious individuals from successfully exploiting programming flaws in the
website?
A. Anti-spam software
B. Application sandboxing
C. Data loss prevention
D. Input validation
Correct Answer: D
QUESTION 2
A developer has implemented a piece of client-side JavaScript code to sanitize a user\\’s provided input to a web page
login screen. The code ensures that only the upper case and lower case letters are entered in the username field, and
that only a 6-digit PIN is entered in the password field. A security administrator is concerned with the following web
server log:
10.235.62.11 ?- [02/Mar/2014:06:13:04] “GET /site/script.php?user=admiand;pass=pass%20or%201=1 HTTP/1.1” 200
5724
Given this log, which of the following is the security administrator concerned with and which fix should be implemented
by the developer?
A. The security administrator is concerned with nonprintable characters being used to gain administrative access, and
the developer should strip all nonprintable characters.
B. The security administrator is concerned with XSS, and the developer should normalize Unicode characters on the
browser side.
C. The security administrator is concerned with SQL injection, and the developer should implement server side input
validation.
D. The security administrator is concerned that someone may log on as the administrator, and the developer should
ensure strong passwords are enforced.
Correct Answer: C
The code in the question is an example of a SQL Injection attack. The code `1=1\\’ will always provide a value of true.
This can be included in statement designed to return all rows in a SQL table.
In this question, the administrator has implemented client-side input validation. Client-side validation can be bypassed. It
is much more difficult to bypass server-side input validation.
SQL injection is a code injection technique, used to attack data-driven applications, in which malicious SQL statements
are inserted into an entry field for execution (e.g. to dump the database contents to the attacker). SQL injection must
exploit a security vulnerability in an application\\’s software, for example, when user input is either incorrectly filtered for
string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly
executed. SQL injection is mostly known as an attack vector for websites but can be used to attack any type of SQL
database.
QUESTION 3
An organization is currently working with a client to migrate data between a legacy ERP system and a cloud-based ERP
tool using a global PaaS provider. As part of the engagement, the organization is performing data deduplication and
sanitization of client data to ensure compliance with regulatory requirements. Which of the following is the MOST likely
reason for the need to sanitize the client data?
A. Data aggregation
B. Data sovereignty
C. Data isolation
D. Data volume
E. Data analytics
Correct Answer: A
QUESTION 4
A system owner has requested support from data owners to evaluate options for the disposal of equipment containing
sensitive data. Regulatory requirements state the data must be rendered unrecoverable via logical means or physically
destroyed.
Which of the following factors is the regulation intended to address?
A. Sovereignty
B. E-waste
C. Remanence
D. Deduplication
Correct Answer: B
QUESTION 5
IT staff within a company often conduct remote desktop sharing sessions with vendors to troubleshoot vendor product-
related issues. Drag and drop the following security controls to match the associated security concern. Options may be
used once or not at all.
Select and Place: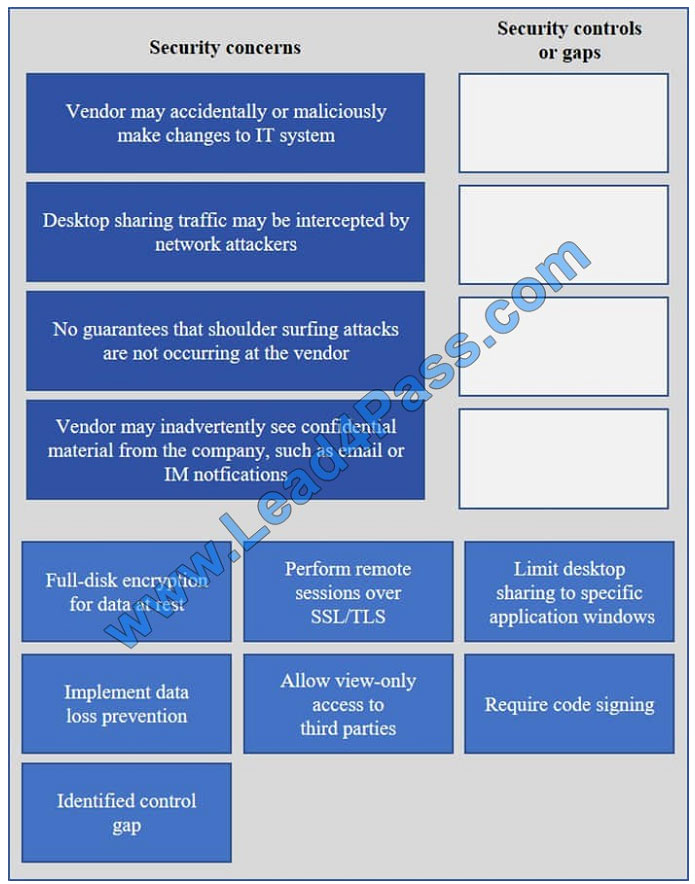
Correct Answer:
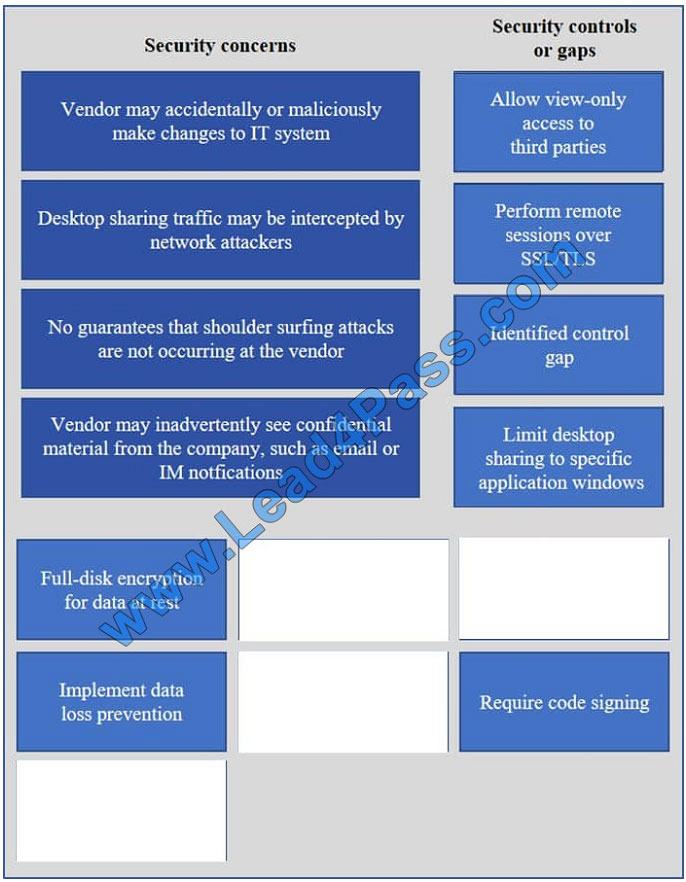
Vendor may accidentally or maliciously make changes to the IT system – Allow view-only access.
With view-only access, the third party can view the desktop but cannot interact with it. In other words, they cannot
control the keyboard or mouse to make any changes.
Desktop sharing traffic may be intercepted by network attackers – Use SSL for remote sessions.
SSL (Secure Sockets Layer) encrypts data in transit between computers. If an attacker intercepted the traffic, the data
would be encrypted and therefore unreadable to the attacker.
No guarantees that shoulder surfing attacks are not occurring at the vendor – Identified control gap.
Shoulder surfing is where someone else gains information by looking at your computer screen. This should be identified
as a risk. A control gap occurs when there are either insufficient or no actions taken to avoid or mitigate a significant
risk.
Vendor may inadvertently see confidential material from the company such as email and IMs – Limit desktop session to
certain windows.
The easiest way to prevent a third party from viewing your emails and IMs is to close the email and IM application
windows for the duration of the desktop sharing session.
QUESTION 6
A security administrator has been asked to select a cryptographic algorithm to meet the criteria of a new application.
The application utilizes streaming video that can be viewed both on computers and mobile devices. The application
designers have asked that the algorithm support the transport encryption with the lowest possible performance
overhead. Which of the following recommendations would BEST meet the needs of the application designers? (Select
TWO).
A. Use AES in Electronic Codebook mode
B. Use RC4 in Cipher Block Chaining mode
C. Use RC4 with Fixed IV generation
D. Use AES with cipher text padding
E. Use RC4 with a nonce generated IV
F. Use AES in Counter mode
Correct Answer: EF
In cryptography, an initialization vector (IV) is a fixed-size input to a cryptographic primitive that is typically required to be
random or pseudorandom. Randomization is crucial for encryption schemes to achieve semantic security, a property
whereby repeated usage of the scheme under the same key does not allow an attacker to infer relationships between
segments of the encrypted message.
Some cryptographic primitives require the IV only to be non-repeating, and the required randomness is derived
internally. In this case, the IV is commonly called a nonce (number used once), and the primitives are described as
stateful as opposed to randomized. This is because the IV need not be explicitly forwarded to a recipient but may be
derived from a common state updated at both sender and receiver side. An example of stateful encryption schemes is
the counter mode of operation, which uses a sequence number as a nonce.
AES is a block cipher. Counter mode turns a block cipher into a stream cipher. It generates the next keystream block by
encrypting successive values of a “counter”. The counter can be any function which produces a sequence which is
guaranteed not to repeat for a long time, although an actual increment-by-one counter is the simplest and most popular.
QUESTION 7
Company Z is merging with Company A to expand its global presence and consumer base. This purchase includes
several offices in different countries. To maintain strict internal security and compliance requirements, all employee
activity may be monitored and reviewed. Which of the following would be the MOST likely cause for a change in this
practice?
A. The excessive time it will take to merge the company\\’s information systems.
B. Countries may have different legal or regulatory requirements.
C. Company A might not have adequate staffing to conduct these reviews.
D. The companies must consolidate security policies during the merger.
Correct Answer: B
QUESTION 8
A user on a virtual machine downloads a large file using a popular peer-to-peer torrent program. The user is unable to
execute the program on their VM. A security administrator scans the VM and detects a virus in the program. The
administrator reviews the hypervisor logs and correlates several access attempts to the time of execution of the virus.
Which of the following is the MOST likely explanation for this behavior?
A. The hypervisor host does not have hardware acceleration enabled and does not allow DEP.
B. The virus scanner on the VM changes file extensions of all programs downloaded via P2P to prevent execution.
C. The virtual machine is configured to require administrator rights to execute all programs.
D. The virus is trying to access a virtual device which the hypervisor is configured to restrict.
Correct Answer: D
QUESTION 9
During an incident involving the company main database, a team of forensics experts is hired to respond to the breach.
The team is in charge of collecting forensics evidence from the company\\’s database server. Which of the following is
the correct order in which the forensics team should engage?
A. Notify senior management, secure the scene, capture volatile storage, capture non-volatile storage, implement chain
of custody, and analyze original media.
B. Take inventory, secure the scene, capture RAM, capture hard drive, implement chain of custody, document, and
analyze the data.
C. Implement chain of custody, take inventory, secure the scene, capture volatile and non-volatile storage, and
document the findings.
CAS-003 VCE Dumps | CAS-003 Practice Test | CAS-003 Braindumps 7 / 10https://www.leads4pass.com/cas-003.html
2019 Latest lead4pass CAS-003 PDF and VCE dumps Download
D. Secure the scene, take inventory, capture volatile storage, capture non-volatile storage, document, and implement
chain of custody.
Correct Answer: D
The scene has to be secured first to prevent contamination. Once a forensic copy has been created, an analyst will
begin the process of moving from most volatile to least volatile information. The chain of custody helps to protect the
integrity and reliability of the evidence by keeping an evidence log that shows all access to evidence, from collection to
appearance in court.
QUESTION 10
A manufacturing company is having issues with unauthorized access and modification of the controls operating the
production equipment. A communication requirement is to allow the free flow of data between all network segments at
the site. Which of the following BEST remediates the issue?
A. Implement SCADA security measures.
B. Implement NIPS to prevent the unauthorized activity.
C. Implement an AAA solution.
D. Implement a firewall to restrict access to only a single management station.
Correct Answer: C
QUESTION 11
A security architect is seeking to outsource company server resources to a commercial cloud service provider. The
provider under consideration has a reputation for poorly controlling physical access to datacenters and has been the
victim of multiple social engineering attacks. The service provider regularly assigns VMs from multiple clients to the
same physical resources. When conducting the final risk assessment which of the following should the security architect
take into consideration?
A. The ability to implement user training programs for the purpose of educating internal staff about the dangers of social
engineering.
B. The cost of resources required to relocate services in the event of resource exhaustion on a particular VM.
C. The likelihood a malicious user will obtain proprietary information by gaining local access to the hypervisor platform.
D. Annual loss expectancy resulting from social engineering attacks against the cloud service provider affecting
corporate network infrastructure.
Correct Answer: C
QUESTION 12
Company A is purchasing Company B, and will import all of Company B\\’s users into its authentication system.
Company A uses 802.1x with a RADIUS server, while Company B uses a captive SSL portal with an LDAP backend.
Which of the following is the BEST way to integrate these two networks?
A. Enable RADIUS and end point security on Company B\\’s network devices.
B. Enable LDAP authentication on Company A\\’s network devices.
C. Enable LDAP/TLS authentication on Company A\\’s network devices.
D. Enable 802.1x on Company B\\’s network devices.
Correct Answer: D
QUESTION 13
A large hospital has implemented BYOD to allow doctors and specialists the ability to access patient medical records on
their tablets. The doctors and specialists access patient records over the hospital\\’s guest WiFi network which is
isolated from the internal network with appropriate security controls. The patient records management system can be
accessed from the guest network and require two factor authentication. Using a remote desktop type interface, the
doctors and specialists can interact with the hospital\\’s system. Cut and paste and printing functions are disabled to
prevent the copying of data to BYOD devices. Which of the following are of MOST concern? (Select TWO).
A. Privacy could be compromised as patient records can be viewed in uncontrolled areas.
B. Device encryption has not been enabled and will result in a greater likelihood of data loss.
C. The guest WiFi may be exploited allowing non-authorized individuals access to confidential patient data.
D. Malware may be on BYOD devices which can extract data via key logging and screen scrapes.
E. Remote wiping of devices should be enabled to ensure any lost device is rendered inoperable.
Correct Answer: AD
Privacy could be compromised because patient records can be from a doctor\\’s personal device. This can then be
shown to persons not authorized to view this information. Similarly, the doctor\\’s personal device could have malware
on it.
Related CAS-003 Popular Exam resources
| title | youtube | CompTIA | lead4pass | Lead4Pass Total Questions | related CompTIA blog | |
|---|---|---|---|---|---|---|
| CompTIA CASP | lead4pass CAS-003 dumps pdf | lead4pass CAS-003 youtube | CompTIA Advanced Security Practitioner (CASP+) | https://www.leads4pass.com/cas-003.html | 491 Q&A | Passontheinfo comptia casp cas-003 exam |
Lead4Pass Year-round Discount Code
What are the advantages of Lead4pass?
Lead4pass employs the most authoritative exam specialists from CompTIA, Microsoft, Cisco, Oracle, EMC, etc. We update exam data throughout the year. Highest pass rate! We have a large user base. We are an industry leader! Choose Lead4Pass to pass the exam with ease!
Summarize:
It’s not easy to pass the CompTIA CAS-003 exam, but with accurate learning materials and proper practice, you can crack the exam with excellent results. https://www.leads4pass.com/cas-003.html provides you with the most relevant learning materials that you can use to help you prepare.