New 200-201 dumps is the newly launched Cisco 200-201 CBROPS Exam Solution reviewed and edited by the Lead4Pass CyberOps Associate certification team, it is real and effective!
Lead4Pass 200-201 dumps: https://www.leads4pass.com/200-201.html Based on the CyberOps Associate exam topic (Security Concepts, Security Monitoring, Host-Based Analysis, Network Intrusion Analysis, Security Policies and Procedures, view the complete topic detail.)
264 latest exam questions and answers have been released, which fully meet the actual exam conditions.
Highlight:
- How about Lead4Pass 200-201 dumps?
- CyberOps Associate 200-201 Exam Overview
- Is Cisco CyberOps worth IT?

Tips: The next update of the CyberOps Associate exam will be on November 21, 2023. The new exam will undergo dramatic changes. Candidates will receive the latest exam materials and meet new challenges!
But there will be no changes to the exams before then!
Practice new 200-201 dumps exam questions online
Lead4Pass 200-201 dumps have been verified in practice and are real and effective! And to dispel doubts, we share a copy of the latest exam questions and answers online! You can verify first before choosing!
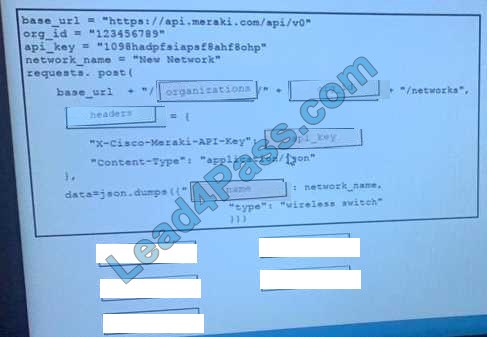
Question 1:
An engineer needs to fetch logs from a proxy server and generate actual events according to the data received. Which technology should the engineer use to accomplish this task?
A. Firepower
B. Email Security Appliance
C. Web Security Appliance
D. Stealthwatch
Correct Answer: C
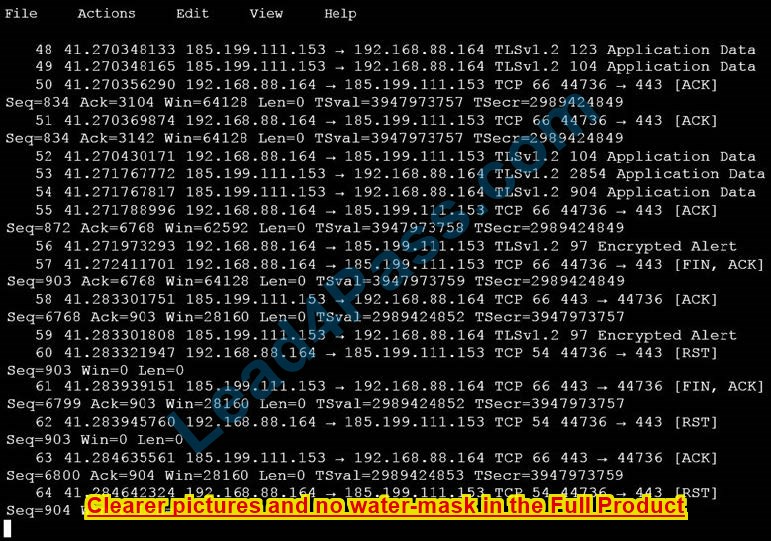
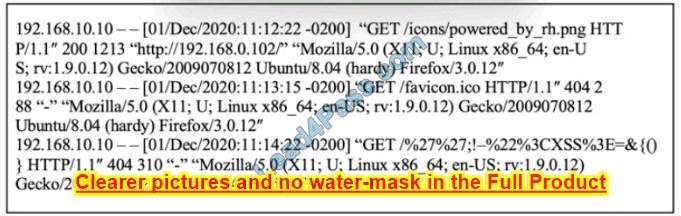
Question 2:
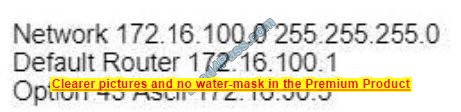
Refer to the exhibit.

Which kind of attack method is depicted in this string?
A. cross-site scripting
B. man-in-the-middle
C. SQL injection
D. denial of service
Correct Answer: A
Question 3:
What are two social engineering techniques? (Choose two.)
A. privilege escalation
B. DDoS attack
C. phishing
D. man-in-the-middle
E. pharming
Correct Answer: CE
Question 4:
Which security principle is violated by running all processes as root or administrator?
A. principle of least privilege
B. role-based access control
C. separation of duties
D. trusted computing base
Correct Answer: A
Question 5:
A security engineer has a video of a suspect entering a data center that was captured on the same day that files in the same data center were transferred to a competitor. Which type of evidence is this?
A. best evidence
B. prima facie evidence
C. indirect evidence
D. physical evidence
Correct Answer: C
There are three general types of evidence:
–> Best evidence: can be presented in court in the original form (for example, an exact copy of a hard disk drive).
–> Corroborating evidence: tends to support a theory or an assumption deduced by some initial evidence. This corroborating evidence confirms the proposition. –> Indirect or circumstantial evidence: extrapolation to a conclusion of fact (such as fingerprints, DNA evidence, and so on).
Question 6:
An engineer is working with the compliance teams to identify the data passing through the network. During analysis, the engineer informs the compliance team that external perimeter data flows contain records, writings, and artwork Internal segregated network flows contain the customer choices by gender, addresses, and product preferences by age. The engineer must identify protected data. Which two types of data must be identified\’? (Choose two.)
A. SOX
B. PII
C. PHI
D. PCI
E. copyright
Correct Answer: BC
Question 7:
While viewing packet capture data, an analyst sees that one IP is sending and receiving traffic for multiple devices by modifying the IP header. Which technology makes this behavior possible?
A. encapsulation
B. TOR
C. tunneling
D. NAT
Correct Answer: D
Network address translation (NAT) is a method of mapping an IP address space into another by modifying network address information in the IP header of packets while they are in transit across a traffic routing device.
Question 8:
Syslog collecting software is installed on the server For the log containment, a disk with FAT type partition is used An engineer determined that log files are being corrupted when the 4 GB tile size is exceeded. Which action resolves the issue?
A. Add space to the existing partition and lower the retention period.
B. Use FAT32 to exceed the limit of 4 GB.
C. Use the Ext4 partition because it can hold files up to 16 TB.
D. Use NTFS partition for log file containment
Correct Answer: D
Question 9:
Which security monitoring data type requires the largest storage space?
A. transaction data
B. statistical data
C. session data
D. full packet capture
Correct Answer: D
Question 10:
What is the impact of encryption?
A. Confidentiality of the data is kept secure and permissions are validated
B. Data is accessible and available to permitted individuals
C. Data is unaltered and its integrity is preserved
D. Data is secure and unreadable without decrypting it
Correct Answer: A
Question 11:
An analyst received a ticket regarding a degraded processing capability for one of the HR department\’s servers. On the same day, an engineer noticed a disabled antivirus software and was not able to determine when or why it occurred. According to the NIST Incident Handling Guide, what is the next phase of this investigation?
A. Recovery
B. Detection
C. Eradication
D. Analysis
Correct Answer: B
Reference: https://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-61r2.pdf
Question 12:
What is the difference between the ACK flag and the RST flag in the NetFlow log session?
A. The RST flag confirms the beginning of the TCP connection, and the ACK flag responds when the data for the payload is complete
B. The ACK flag confirms the beginning of the TCP connection, and the RST flag responds when the data for the payload is complete
C. The RST flag confirms the receipt of the prior segment, and the ACK flag allows for the spontaneous termination of a connection
D. The ACK flag confirms the receipt of the prior segment, and the RST flag allows for the spontaneous termination of a connection
Correct Answer: D
Question 13:
What is the practice of giving an employee access to only the resources needed to accomplish their job?
A. principle of least privilege
B. organizational separation
C. separation of duties
D. needs to know the principle
Correct Answer: A
Question 14:
An engineer is investigating a case of the unauthorized usage of the “Tcpdump” tool. The analysis revealed that a malicious insider attempted to sniff traffic on a specific interface. What type of information did the malicious insider attempt to obtain?
A. tagged protocols being used on the network
B. all firewall alerts and resulting mitigations
C. tagged ports being used on the network
D. all information and data within the datagram
Correct Answer: C
Question 15:
What makes HTTPS traffic difficult to monitor?
A. SSL interception
B. packet header size
C. signature detection time
D. encryption
Correct Answer: D
…
CyberOps Associate 200-201 Exam Overview
| Exam name: | Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) |
| Exam code: | 200-201 |
| Duration: | 120 Minutes |
| Languages: | English |
| Price: | 300$ |
| Number of Questions: | 95-105 |
| Passing Score: | 750-850 / 1000 Approx |
| Questions types: | Multiple choice (single and multiple answers) Drag-and-drop. Simulation. Fill-in-the-blank. Router and Switch Configuration Questions. Troubleshooting Questions. Testlet. Short Answer Questions. |
| Way to register: | In-person, Pearson VUE |
Is Cisco CyberOps worth IT?
The value of Cisco CyberOps certification depends on many aspects, based on past experience:
If you are interested in a career in cybersecurity, the Cisco CyberOps certification is well worth it. It provides a foundation in cybersecurity concepts, skills, and practices, making it a good choice for those looking to enter the field.
Many employers look for certifications like Cisco CyberOps when hiring for cybersecurity roles, and having this certification can help you stand out among candidates
For individuals already working in IT, earning a Cisco CyberOps certification can provide opportunities for career advancement. It can qualify you to work as a security analyst, security operations center (SOC) analyst, or other cybersecurity positions
Summarize:
All in all! The new 200-201 dumps fully meet the requirements of the CyberOps Associate certification exam and guarantee you a successful pass.
therefore! Use the newly launched Cisco 200-201 CBROPS Exam Solution and download the upgraded version 200-201 dumps: https://www.leads4pass.com/200-201.html (PDF and VCE auxiliary learning tools are provided) to ensure your ease of passing the exam.