The latest updated and revised CompTIA PT0-001 exam questions and answers come from Lead4Pass! Complete CompTIA PT0-001 dumps certification questions!
Welcome to download the latest Lead4Pass CompTIA PT0-001 dumps with PDF and VCE: https://www.leads4pass.com/pt0-001.html (258 Q&A)
[CompTIA PT0-001 dumps pdf] CompTIA PT0-001 dumps PDF uploaded from google drive, online download provided by the latest update of Lead4pass:
https://drive.google.com/file/d/1DHqsHNHXdDwNVKJDECqB8p-YwM4rkz1t/
Latest update CompTIA PT0-001 exam questions and answers online practice test
QUESTION 1
A penetration tester is performing an annual security assessment for a repeat client The tester finds indicators of
previous compromise Which of the following would be the most logical steps to follow NEXT?
A. Report the incident to the tester\\’s immediate manager and follow up with the client immediately
B. Report the incident to the clients Chief Information Security Officer (CISO) immediately and alter the terms of
engagement accordingly
C. Report the incident to the client\\’s legal department and then follow up with the client\\’s security operations team
D. Make note of the anomaly, continue with the penetration testing and detail it in the final report
Correct Answer: A
QUESTION 2
An energy company contracted a security firm to perform a penetration test of a power plant, which employs ICS to
manage power generation and cooling. Which of the following is a consideration unique to such an environment that
must be made by the firm when preparing for the assessment?
A. Selection of the appropriate set of security testing tools
B. Current and load ratings of the ICS components
C. Potential operational and safety hazards
D. Electrical certification of hardware used in the test
Correct Answer: A
QUESTION 3
A penetration tester has performed a pivot to a new Linux device on a different network. The tester writes the following
command:
for m in {1..254..1};do ping -c 1 192.168.101.$m; done
Which of the following BEST describes the result of running this command?
A. Port scan
B. Service enumeration
C. Live host identification
D. Denial of service
Correct Answer: C
QUESTION 4
During a full-scope security assessment, which of the following is a prerequisite to social engineer a target by physically
engaging them?
A. Locating emergency exits
B. Preparing a pretext
C. Shoulder surfing the victim
D. Tailgating the victim
Correct Answer: B
QUESTION 5
A company has engaged a penetration tester to perform an assessment for an application that resides in the
company\\’s DMZ. Prior to conducting testing, in which of the following solutions should the penetration tester\\’s IP
address be whitelisted?
A. WAF
B. HIDS
C. NIDS
D. DLP
Correct Answer: C
QUESTION 6
A penetration tester is perform initial intelligence gathering on some remote hosts prior to conducting a vulnerability
A. The network is submitted as a /25 or greater and the tester needed to access hosts on two different subnets
B. The tester is trying to perform a more stealthy scan by including several bogus addresses
C. The scanning machine has several interfaces to balance the scan request across at the specified rate
D. A discovery scan is run on the first set of addresses, whereas a deeper, more aggressive scan is run against the
latter host.
Correct Answer: B
QUESTION 7
A penetration tester is reviewing the following output from a wireless sniffer: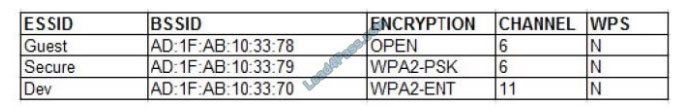
Which of the following can be extrapolated from the above information?
A. Hardware vendor
B. Channel interference
C. Usernames
D. Key strength
Correct Answer: C
QUESTION 8
A vulnerability scan identifies that an SSL certificate does not match the hostname; however, the client disputes the
finding. Which of the following techniques can the penetration tester perform to adjudicate the validity of the findings?
A. Ensure the scanner can make outbound DNS requests.
B. Ensure the scanner is configured to perform ARP resolution.
C. Ensure the scanner is configured to analyze IP hosts.
D. Ensure the scanner has the proper plug -ins loaded.
Correct Answer: A
QUESTION 9
A penetration tester ran an Nmap scan against a target and received the following output: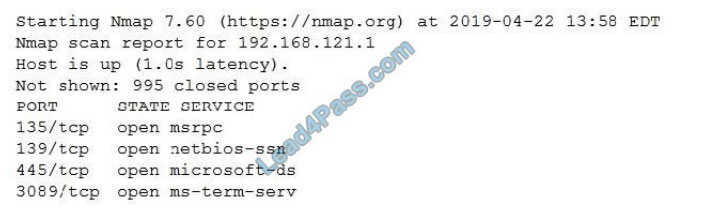
Which of the following commands would be best for the penetration tester to execute NEXT to discover any weaknesses
or vulnerabilities?
A. onesixtyone ? 192.168.121.1
B. enum4linux ? 192.168.121.1
C. snmpwalk ? public 192.168.121.1
D. medusa ? 192.168.121.1 ? users.txt ? passwords.txt ? ssh
Correct Answer: C
QUESTION 10
During a penetration test, a tester identifies traditional antivirus running on the exploited server. Which of the following
techniques would BEST ensure persistence in a post-exploitation phase?
A. Shell binary placed in C:\windows\temp
B. Modified daemons
C. New user creation
D. Backdoored executables
Correct Answer: B
QUESTION 11
A penetration tester has run multiple vulnerability scans against a target system. Which of the following would be unique
to a credentialed scan?
A. Exploits for vulnerabilities found
B. Detailed service configurations
C. Unpatched third-party software
D. Weak access control configurations
Correct Answer: A
QUESTION 12
After several attempts, an attacker was able to gain unauthorized access through a biometric sensor using the
attacker\\’s actual fingerprint without exploitation. Which of the following is the MOST likely of what happened?
A. The biometric device is tuned more toward false positives
B. The biometric device is configured more toward true negatives
C. The biometric device is set to fail closed
D. The biometnc device duplicated a valid user\\’s fingerpnnt.
Correct Answer: A
QUESTION 13
Which of the following types of intrusion techniques is the use of an “under-the-door tool” during a physical security
assessment an example of?
A. Lockpicking
B. Egress sensor triggering
C. Lock bumping
D. Lock bypass
Correct Answer: D
Reference: https://www.triaxiomsecurity.com/2018/08/16/physical-penetration-test- examples/
Update the latest valid CompTIA PT0-001 test questions and answers throughout the year.
Upload the latest PT0-001 exam practice questions and PT0-001 PDF for free every month. Get the complete PT0-001 Brain Dumps,
the latest updated exam questions and answers come from Lead4Pass! For information about Lead4pass PT0-001 Dumps (including PDF and VCE),
please visit: https://www.leads4pass.com/pt0-001.html (PDF + VCE)
ps. Get free CompTIA PT0-001 dumps PDF online: https://drive.google.com/file/d/1DHqsHNHXdDwNVKJDECqB8p-YwM4rkz1t/