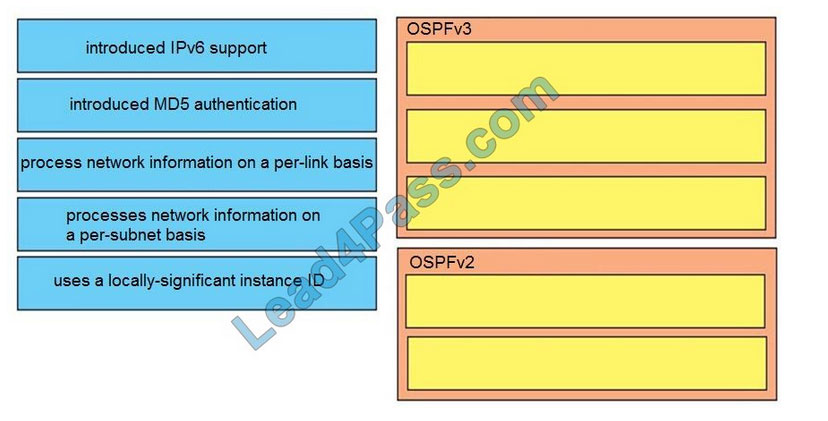
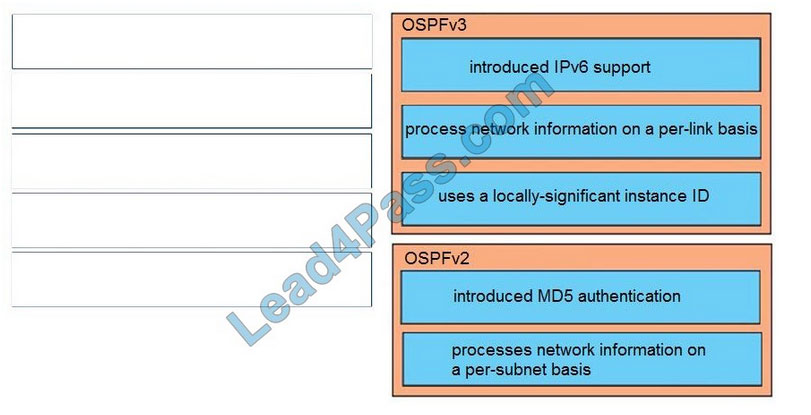
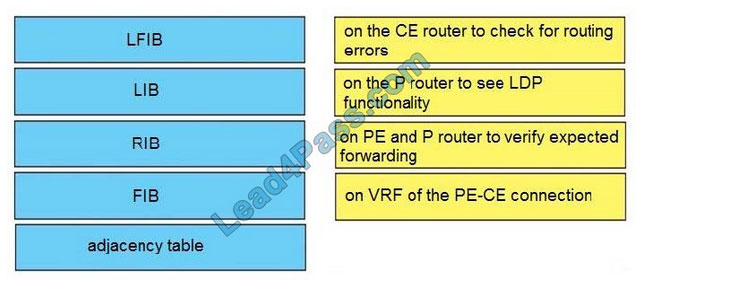
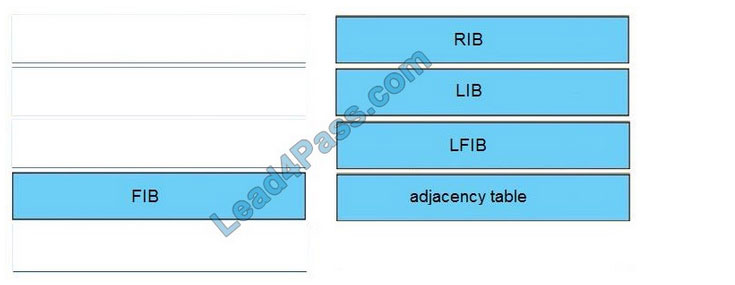
CyberOps Associate 200-201 Dumps is the Cisco 200-201 CBROPS exam material for launching your career in cybersecurity operations.
Lead4Pass 200-201 Dumps Prepares Candidates for Cisco CBROPS Exam Questions and Answers
https://www.leads4pass.com/200-201.html helps you earn the Cisco CyberOps Associate Exam Certification.
Cisco technology is spread all over the world. This means that CyberOps Associate-certified professionals will continue to be sought after, as long as you ensure that you can successfully achieve the CyberOps Associate 200-201 certification. Use the CyberOps Associate 200-201 dumps to guarantee your success with the Cisco CyberOps Associate exam certification.
CyberOps Associate exam FAQs: About, Value, Exam Material
About 200-201 CBROPS: What You Need to Know
Vendor: Cisco
Exam Code: 200-201
Exam Name: Threat Hunting and Defending using Cisco Technologies for CyberOps (CBROPS)
Certification: CyberOps Associate
Languages: English
Price: $300 USD
Duration: 120 mins
Number of Questions: 95-105 questions
Passing score: 80% Approx
200-201 dumps: https://www.leads4pass.com/200-201.html (CyberOps Associate exam dumps maps to Cisco 200-201 CBROPS exam objectives)
200-201 dumps (Number of Questions): 264 Q&A
Last update time: Nov 02, 2022
Is CyberOps Associate certification worth it?
The Cisco Certified CyberOps Associate is regarded by many as a great starting point for cyber security professionals. For instance, it offers enough entry-level fundamental concepts such as cryptography and Security Operations Center (SOC) basics. One of the best things about this cert is the fact that it doesn’t have any prerequisites.
For someone looking to break into cybersecurity, the Cisco Certified CyberOps Associate makes sense. It covers key concepts around Cisco hardware and software, but not in too much detail. Cisco Certified CyberOps Associate also teaches you about security operations and is a good way to land a junior analyst role in a SOC.
–source: https://www.cbtnuggets.com/blog/certifications/cisco/new-cisco-certs-ccna-cyberops-vs-ccnp-security
Free share of a portion of the CyberOps Associate 200-201 CBROPS exam material
| Number of exam questions | Exam name | From | Release time | [Free share] Update Nov 2022 |
| 15 | Threat Hunting and Defending using Cisco Technologies for CyberOps (CBROPS) | Lead4pass | Oct 04, 2022 | 200-201 exam questions 16-28 |
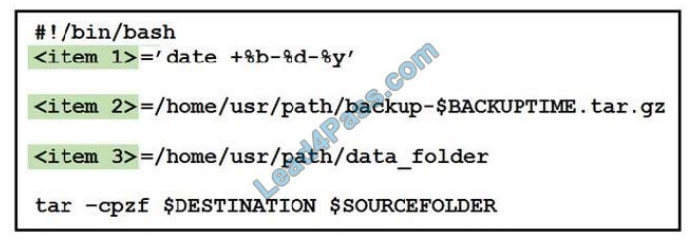
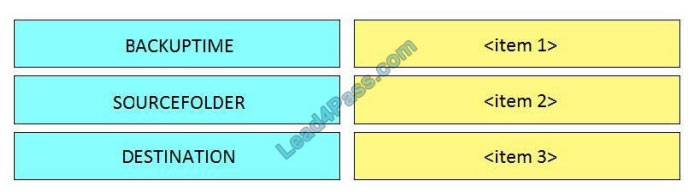
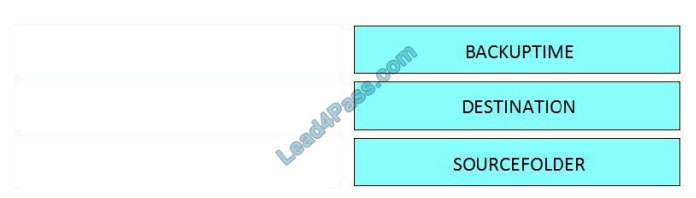
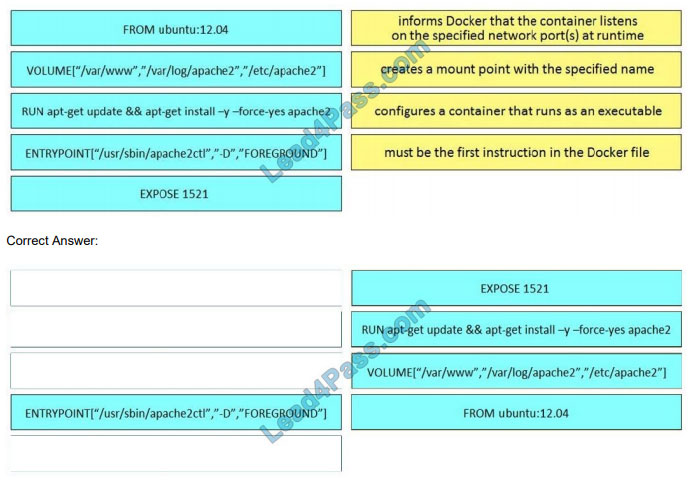
New Question 1:
An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network. What is the impact of this traffic?
A. ransomware communicating after infection
B. users downloading copyrighted content
C. data exfiltration
D. user circumvention of the firewall
Correct Answer: D
New Question 2:
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
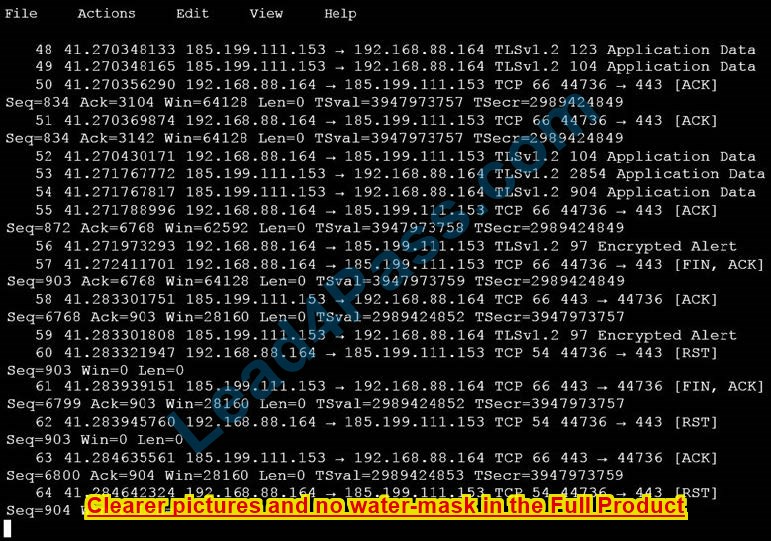
Which obfuscation technique is the attacker using?
A. Base64 encoding
B. TLS encryption
C. SHA-256 hashing
D. ROT13 encryption
Correct Answer: B
ROT13 is considered weak encryption and is not used with TLS (HTTPS:443). Source: https://en.wikipedia.org/wiki/ROT13
New Question 3:
Which technology on a host is used to isolate a running application from other applications?
A. sandbox
B. application allows list
C. application block list
D. host-based firewall
Correct Answer: A
New Question 4:
How does an attack surface differ from an attack vector?
A. An attack vector recognizes the potential outcomes of an attack, and the attack surface is choosing a method of attack.
B. An attack surface identifies vulnerable parts for an attack, and an attack vector specifies which attacks are feasible to those parts.
C. An attack surface mitigates external vulnerabilities, and an attack vector identifies mitigation techniques and possible workarounds.
D. An attack vector matches components that can be exploited, and an attack surface classifies the potential path for exploitation
Correct Answer: B
New Question 5:
An analyst received an alert on their desktop computer showing that an attack was successful on the host. After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
A. The computer has a HIPS installed on it.
B. The computer has a NIPS installed on it.
C. The computer has a HIDS installed on it.
D. The computer has a NIDS installed on it.
Correct Answer: C
New Question 6:
A user received a targeted spear-phishing email and identified it as suspicious before opening the content. To which category of the Cyber Kill Chain model does to this type of event belong?
A. weaponization
B. delivery
C. exploitation
D. reconnaissance
Correct Answer: B
New Question 7:
What is the difference between tampered and untampered disk images?
A. Tampered images have the same stored and computed hash.
B. Untampered images are deliberately altered to preserve evidence.
C. Tampered images are used as evidence.
D. Untampered images are used for forensic investigations.
Correct Answer: D
The disk image must be intact for forensics analysis. As a cybersecurity professional, you may be given the task of capturing an image of a disk in a forensic manner. Imagine a security incident has occurred on a system and you are required to perform some forensic investigation to determine who and what caused the attack. Additionally, you want to ensure the data that was captured is not tampered with or modified during the creation of a disk image process. Ref: Cisco Certified CyberOps Associate 200-201 Certification Guide
New Question 8:
What is the difference between an attack vector and an attack surface?
A. An attack surface identifies vulnerabilities that require user input or validation; and an attack vector identifies vulnerabilities that are independent of user actions.
B. An attack vector identifies components that can be exploited, and an attack surface identifies the potential path an attack can take to penetrate the network.
C. An attack surface recognizes which network parts are vulnerable to an attack, and an attack vector identifies which attacks are possible with these vulnerabilities.
D. An attack vector identifies the potential outcomes of an attack, and an attack surface launches an attack using several methods against the identified vulnerabilities.
Correct Answer: C
New Question 9:
Which process is used when IPS events are removed to improve data integrity?
A. data availability
B. data normalization
C. data signature
D. data protection
Correct Answer: B
New Question 10:
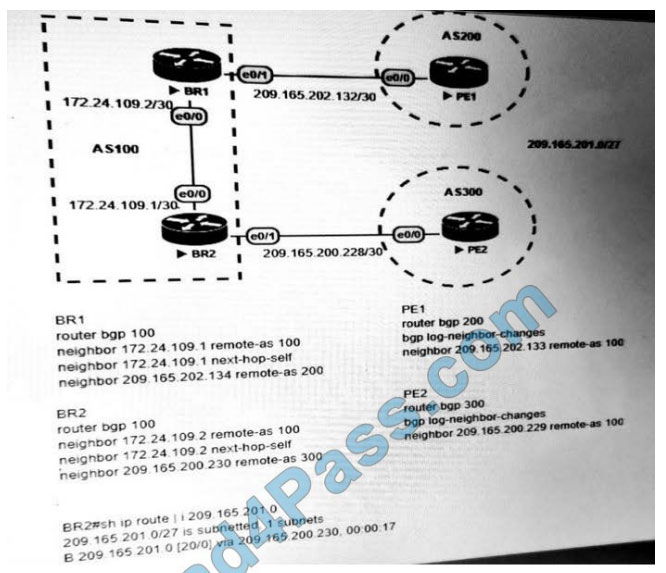
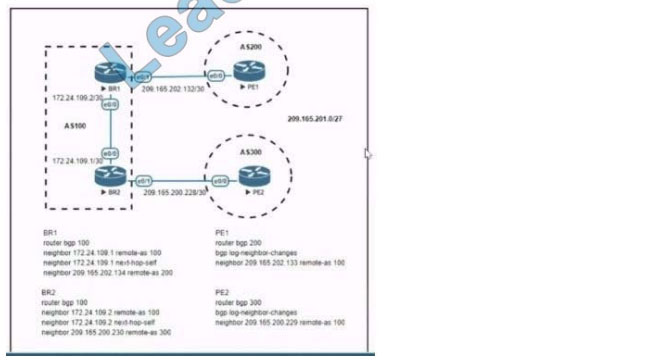
Refer to the exhibit.
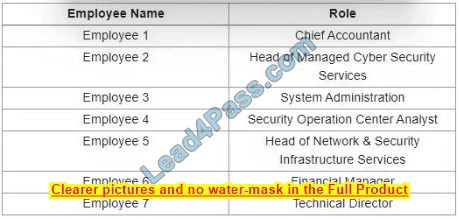
Which stakeholders must be involved when a company workstation is compromised?
A. Employee 1 Employee 2, Employee 3, Employee 4, Employee 5, Employee 7
B. Employee 1, Employee 2, Employee 4, Employee 5
C. Employee 4, Employee 6, Employee 7
D. Employee 2, Employee 3, Employee 4, Employee 5
Correct Answer: D
New Question 11:
What is the function of a command and control server?
A. It enumerates open ports on a network device
B. It drops secondary payload into malware
C. It is used to regain control of the network after a compromise
D. It sends instructions to a compromised system
Correct Answer: D
New Question 12:
At which layer is deep packet inspection investigated on a firewall?
A. internet
B. transport
C. application
D. data link
Correct Answer: C
A deep packet inspection is a form of packet filtering usually carried out as a function of your firewall. It is applied at the Open Systems Interconnection\’s application layer. Deep packet inspection evaluates the contents of a packet that is going through a checkpoint.
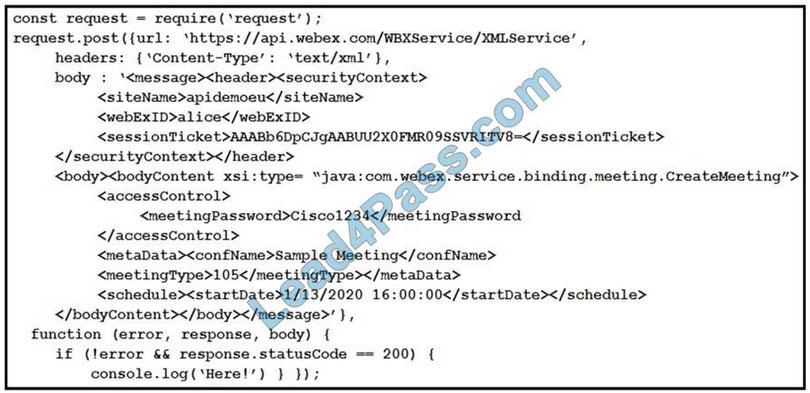
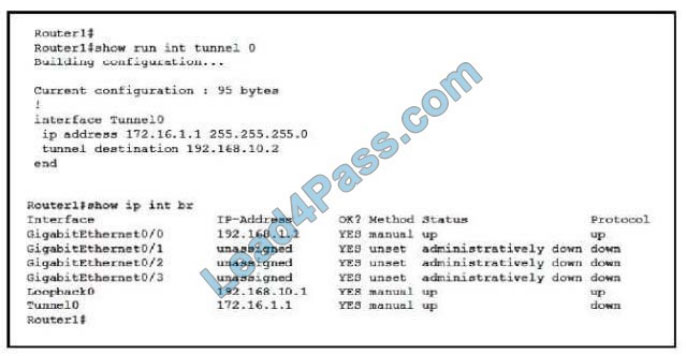
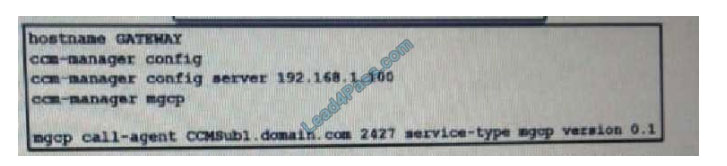
New Question 13:
Refer to the exhibit.
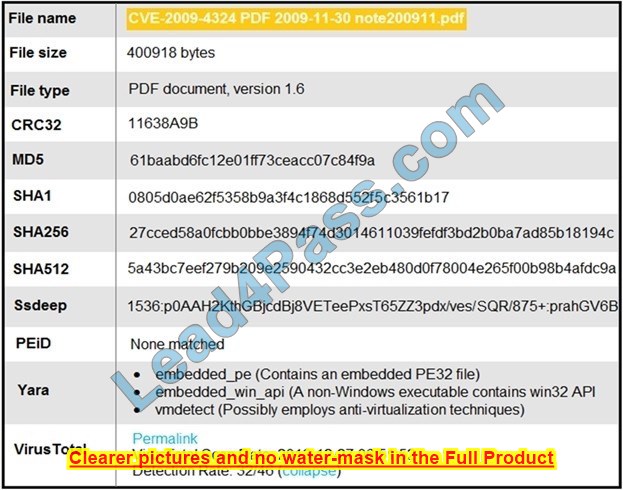
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?
A. The file has an embedded executable and was matched by PEiD threat signatures for further analysis.
B. The file has an embedded non-Windows executable but no suspicious features are identified.
C. The file has an embedded Windows 32 executable and the Yara field lists suspicious features for further analysis.
D. The file was matched by PEiD threat signatures but no suspicious features are identified since the signature list is up to date.
Correct Answer: C
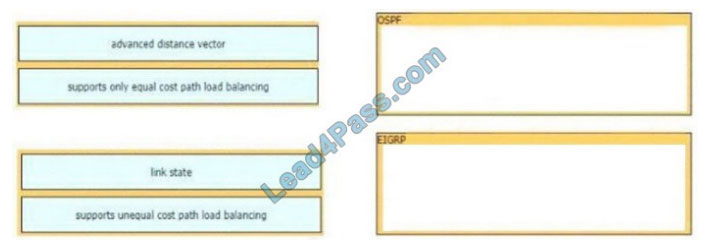
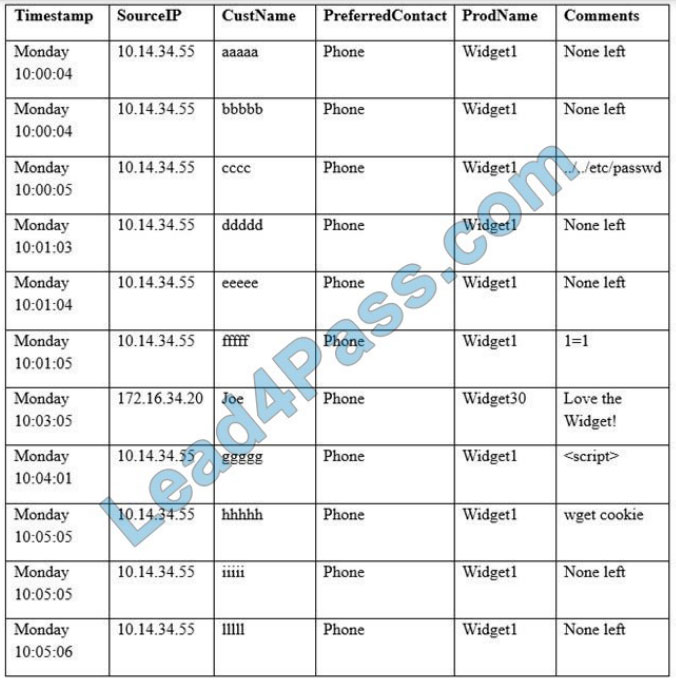
New Question 14:
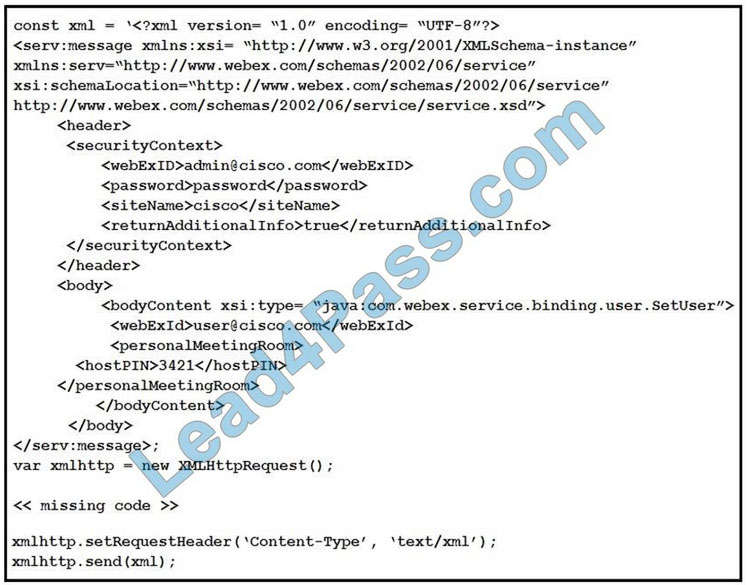
Refer to the exhibit.
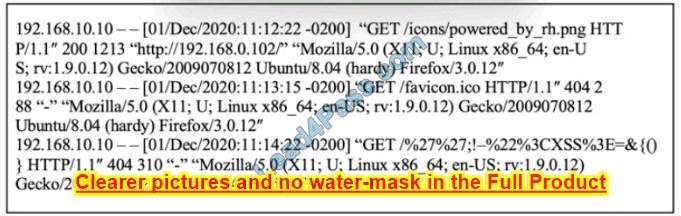
What is occurring?
A. Cross-Site Scripting attack
B. XML External Entitles attack
C. Insecure Deserialization
D. Regular GET requests
Correct Answer: B
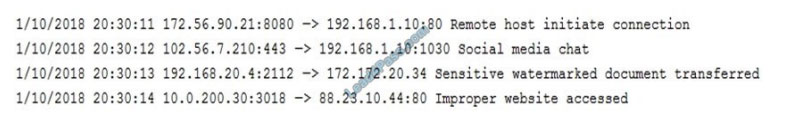
New Question 15:
Refer to the exhibit.
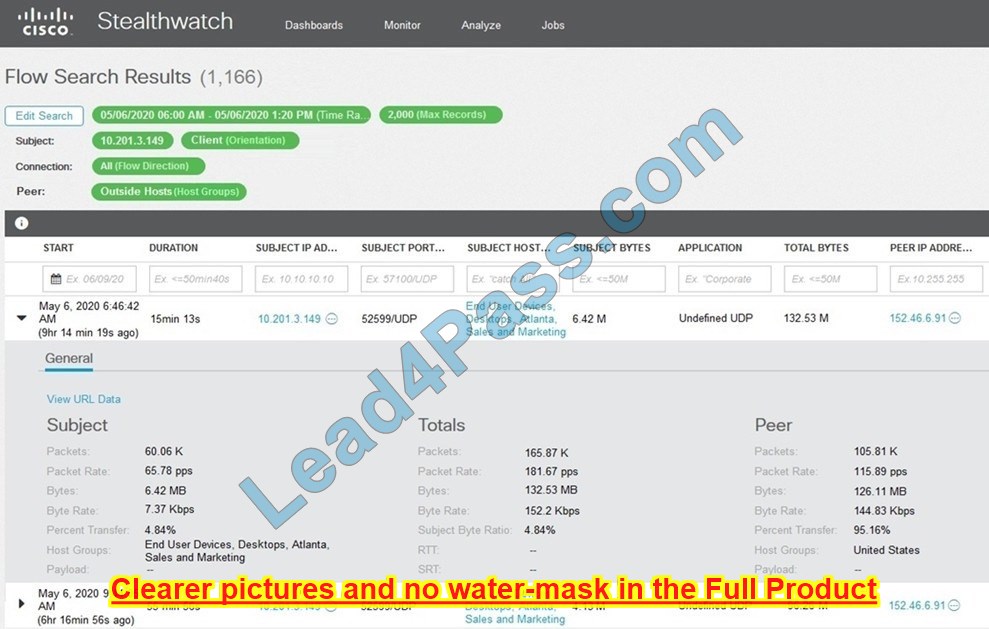
What is the potential threat identified in this Stealthwatch dashboard?
A. Host 10.201.3.149 is sending data to 152.46.6.91 using TCP/443.
B. Host 152.46.6.91 is being identified as a watchlist country for data transfer.
C. Traffic to 152.46.6.149 is being denied by an Advanced Network Control policy.
D. Host 10.201.3.149 is receiving almost 19 times more data than is being sent to host 152.46.6.91.
Correct Answer: D
…
[16-28] New 200-201 exam questions PDF download: https://drive.google.com/file/d/1jiweTttTSynQKmfr1o7J_vTVYc49oIUI/
[Free Download]CyberOps Associate 200-201 CBROPS exam material:
https://drive.google.com/file/d/17f3pPGSHs6kDYRM2C8mTea8RPZ7QLQ6z/view?usp=sharing
https://drive.google.com/file/d/1NvgnmVOH2wzbAtjRlNnpN57M70GgdSeW/view?usp=sharing
https://drive.google.com/file/d/1Hq9tXhs7kyJzL3cTTXNNYoTOKZOld2X7/view?usp=sharing
The above are free to share 15 200-201 CBROPS exam material, [200-201 dumps: Update Nov 2022] click here to get more exam questions and answers.