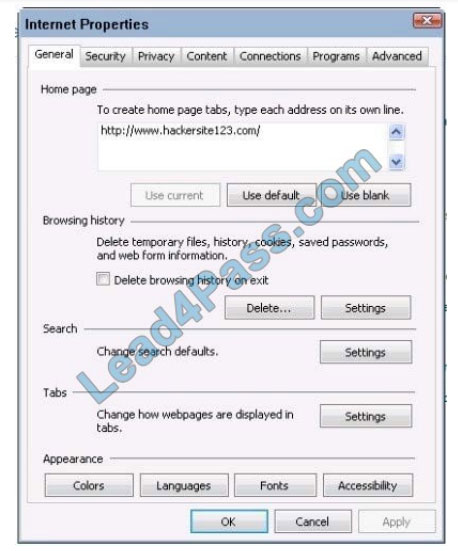
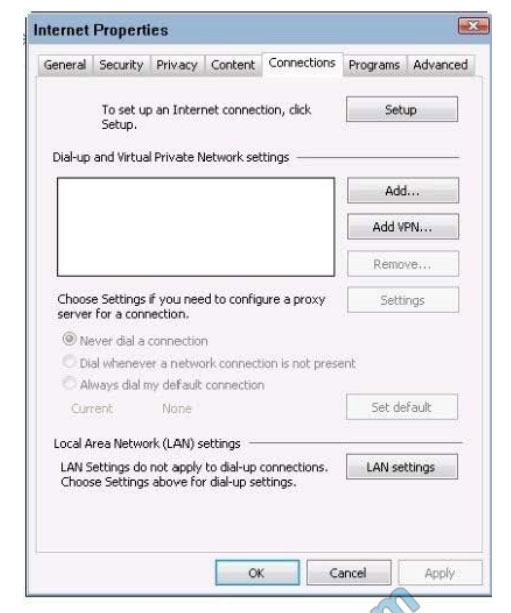
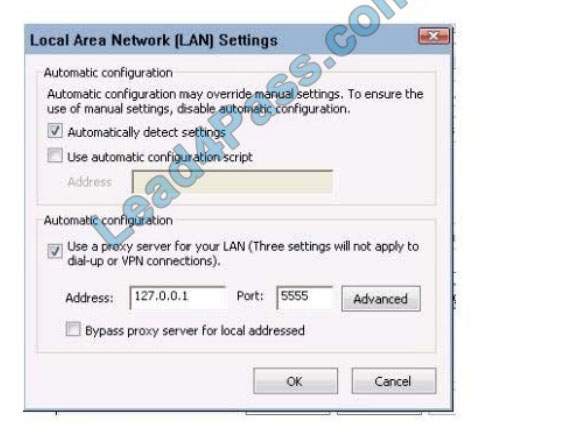
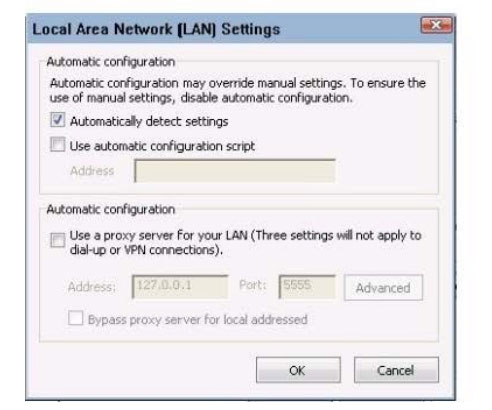
The latest updated CompTIA XK0-004 exam dumps and free XK0-004 exam practice questions and answers! Latest updates from Lead4Pass CompTIA XK0-004 Dumps PDF and XK0-004 Dumps VCE, Lead4Pass XK0-004 exam questions updated and answers corrected! Get the full CompTIA XK0-004 dumps from https://www.leads4pass.com/xk0-004.html (VCE&PDF)
Latest XK0-004 PDF for free
Share the CompTIA XK0-004 Dumps PDF for free From Lead4pass XK0-004 Dumps part of the distraction collected on Google Drive shared by Lead4pass
https://drive.google.com/file/d/1iayVLHhMJ0IymfKzF1Zq8UTUVdul-_OV/
The latest updated CompTIA XK0-004 Exam Practice Questions and Answers Online Practice Test is free to share from Lead4Pass (Q1-Q13)
QUESTION 1
An administrator needs to create a shared directory in which all users are able, write, and execute its content but none
of the regular users are able to delete any content. Which of the following permissions should be applied to this shared
directory?
A. rwxrwxrwt
B. rwxrwxrws
C. rwxrwxrwx
D. rwxrwxrw*
Correct Answer: C
QUESTION 2
A Linux administrator wants to obtain a list of files and subdirectories in the /etc directory that contain the word
“services”. Once the files and subdirectories are discovered, they should be listed alphabetically in the
/var/tmp/foundservices file. Which of the following shell scripts will accomplish this task?
A. #/bin/bashfind /etc –name services | sort > /var/tmp/foundservices
B. #/bin/bashlocate /etc –sort –name services > /var/tmp/foundservices
C. #/bin/bashfind –name services –sort /var/tmp/foundservices
Correct Answer: B
QUESTION 3
Which of the following commands would show the default printer on a Linux system?
A. lpr
B. lpq
C. lpstat
D. lspci
Correct Answer: B
Reference: https://superuser.com/questions/123576/show-default-linux-printer
QUESTION 4
An administrator notices a directory on a web server named /var/www/html/old_reports that should no longer be
accessible on the web. Which of the following commands will accomplish this task?
A. chmod 000 /var/www/html/old_reports
B. chgrp root /var/www/html/old_reports
C. chown apache /var/www/html/old_reports
D. setenforce apache /var/www/html/old_reports
Correct Answer: D
QUESTION 5
A Linux administrator needs to switch from text mode to GUI. Which of the following run levels will start the GUI by
default?
A. Runlevel 3
B. Runlevel 4
C. Runlevel 5 D. Runlevel 6
Correct Answer: C
Reference: http://www.linfo.org/runlevel_def.html
QUESTION 6
DRAG DROP
The lead Linux has added a disk, /dev/sdd, to a VM that is running out of disk space. Place the following steps in the
correct order from first (1) to last (4) to add the disk to the existing LVM.
Select and Place:
![[2021.3] lead4pass xk0-004 practice test q6](https://www.braindump4it.com/wp-content/uploads/2021/03/q6.jpg)
Correct Answer:
![[2021.3] lead4pass xk0-004 practice test q6-1](https://www.braindump4it.com/wp-content/uploads/2021/03/q6-1.jpg)
QUESTION 7
A junior Linux administrator is installing a new application with CPU architecture requirements that have the following
specifications: x64 bit 3.0GHz speed Minimum quad-core The administrator wants to leverage existing equipment but is
unsure whether the requirements of these systems are adequate. The administrator issues the following command
cat/proc/cpuinfo. The output of the command is as follows:![[2021.3] lead4pass xk0-004 practice test q7](https://www.braindump4it.com/wp-content/uploads/2021/03/q7.jpg)
Which of the following is the recommended course of action the administrator should take based on this output?
A. Install the application, as the system meets the application requirements
B. Procure new equipment that matches the recommended specifications
C. Recompile the Linux kernel to support the installation.
D. Reconfigure lib modules to support the new application.
Correct Answer: A
QUESTION 8
After starting a long-running script, a systems administrator needs to verify the frequency of what is filling up the /var
partition and kill it because it is consuming too much space. Which of the following is the correct sequence given only a
terminal is available?
A. 1. CTRL-C2. bg3. watch df /var4. CTRL-C5. fg6. CTRL-Z
B. 1. CTRL-C2. fg3. watch df /var4. CTRL-Z5. bg6. CTRL-Z
C. 1. CTRL-Z2. bg3. watch df /var4. CTRL-C5. fg6. CTRL-C
D. 1. CTRL-Z2. bg3. watch df /var4. CTRL-Z5. fg6. CTRL-C
Correct Answer: D
QUESTION 9
A Linux administrator needs to schedule a cron job to run at 1:15 p.m. every Friday to report the amount of free disk
space on the system and to send the output to a file named “freespace”. Which of the following would meet this
requirement?
A. 13 15 * * 5 df > /freespace
B. 15 13 * * 5 df > /freespace
C. 15 1 * * 6 df > /freespace
D. 15 13 6 * * df > /freespace
Correct Answer: A
QUESTION 10
Joe, a member of the accounting group on a Linux system, is unable to write a file called “taxes” in the accounting
shared directory. The ownership and permissions on the directory and file are as follows: accounting drwxrw-r– user =
ann, group = accounting taxes -rw-r–r– , user = ann, group = accounting
Which of the following commands would allow Joe to write to the file? (Choose two.)
A. chmod g+x accounting
B. chmod 777 taxes
C. chgrp taxes accounting
D. chgrp accounting taxes
E. chmod 774 accounting
F. chmod u+x accounting
Correct Answer: AF
Reference: https://www.pluralsight.com/blog/it-ops/linux-file-permissions
QUESTION 11
A junior Linux administrator needs to ensure service will start on system boot. Which of the following commands
should be used to accomplish this task?
A. chkconfig on
B. systemctl bootup
C. service enable
D. crontab install
Correct Answer: A
Reference: https://geekflare.com/how-to-auto-start-services-on-boot-in-linux/
QUESTION 12
A systems administrator is enabling quotas on the /home directory of a Linux server. The administrator makes the
appropriate edits to the /etc/fstab file and attempts to issue the commands to enable quotas on the desired directory.
However, the administrator receives an error message stating the filesystem does not support quotas. Which of the
following commands should the administrator perform to proceed?
A. mount o remount /home
B. quotacheck -cg
C. edquota /home
D. quotaon /home
Correct Answer: D
Reference: https://www.tecmint.com/set-filesystem-disk-quotas-on-ubuntu/
QUESTION 13
A networked has been crashing intermittently. A Linux administrator would like to write a shell script that will attempt to
ping the server and email an alert if the server fails to respond. The script will later be scheduled via cron job. Which of
the following scripts would BEST accomplish this task?![[2021.3] lead4pass xk0-004 practice test q13](https://www.braindump4it.com/wp-content/uploads/2021/03/q13.jpg)
A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: D
Braindump4it shares the latest updated CompTIA XK0-004 exam exercise questions, XK0-004 dumps pdf for free.
All exam questions and answers come from the Lead4pass exam dumps shared part! Lead4pass updates throughout the year and shares a portion of your exam questions for free to help you understand the exam content and enhance your exam experience!
Get the full CompTIA XK0-004 exam dumps questions at: https://www.leads4pass.com/xk0-004.html (pdf&vce)
ps.
Get free CompTIA XK0-004 dumps PDF online: https://drive.google.com/file/d/1iayVLHhMJ0IymfKzF1Zq8UTUVdul-_OV/

![[2021.3] lead4pass sy0-601 practice test q2](https://www.braindump4it.com/wp-content/uploads/2021/03/q2-4.jpg)
![[2021.3] lead4pass sy0-601 practice test q2-1](https://www.braindump4it.com/wp-content/uploads/2021/03/q2-1-1.jpg)
![[2021.3] lead4pass sy0-601 practice test q2-2](https://www.braindump4it.com/wp-content/uploads/2021/03/q2-2-1.jpg)
![[2021.3] lead4pass sy0-601 practice test q9](https://www.braindump4it.com/wp-content/uploads/2021/03/q9.jpg)
![[2021.3] lead4pass sy0-601 practice test q9-1](https://www.braindump4it.com/wp-content/uploads/2021/03/q9-1.jpg)
![[2021.3] lead4pass sy0-601 practice test q9-3](https://www.braindump4it.com/wp-content/uploads/2021/03/q9-3.jpg)
![[2021.3] lead4pass sy0-601 practice test q9-2](https://www.braindump4it.com/wp-content/uploads/2021/03/q9-2.jpg)

![[2021.3] lead4pass sy0-501 practice test q3](https://www.braindump4it.com/wp-content/uploads/2021/03/q3.jpg)
![[2021.3] lead4pass sy0-501 practice test q10](https://www.braindump4it.com/wp-content/uploads/2021/03/q10.jpg)
![[2021.3] lead4pass sy0-501 practice test q10-1](https://www.braindump4it.com/wp-content/uploads/2021/03/q10-1.jpg)

![[2021.3] lead4pass pk0-004 practice test q12](https://www.braindump4it.com/wp-content/uploads/2021/03/q12.jpg)



![[2021.3] lead4pass cs0-002 practice test q4](https://www.braindump4it.com/wp-content/uploads/2021/03/q4.jpg)
![[2021.3] lead4pass cs0-002 practice test q5](https://www.braindump4it.com/wp-content/uploads/2021/03/q5.jpg)


![[2021.3] lead4pass cas-003 practice test q1](https://www.braindump4it.com/wp-content/uploads/2021/03/q1.jpg)