The latest updated and revised CompTIA CV0-003 exam questions and answers come from Lead4Pass! Complete CompTIA CV0-003 dumps certification questions!
Welcome to download the latest Lead4Pass CompTIA CV0-003 dumps with PDF and VCE: https://www.leads4pass.com/cv0-003.html (142 Q&A)
[CompTIA CV0-003 dumps pdf] CompTIA CV0-003 dumps PDF uploaded from Braindump4it, online download provided by the latest update of Lead4pass:
https://www.braindump4it.com/wp-content/uploads/2021/07/Lead4pass-CompTIA-Cloud-Plus-CV0-003-Exam-Dumps-Braindumps-PDF-VCE.pdf
Latest update CompTIA CV0-003 exam questions and answers online practice test
QUESTION 1
Given the metric below: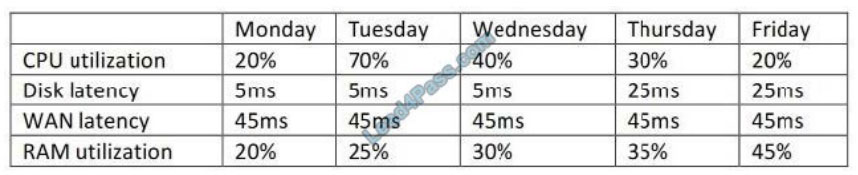
Using iSCSI storage reports across three datacenters, which of the following recorded metrics indicates an anomaly in
the performance?
A. Disk latency
B. CPU utilization
C. WAN latency
D. RAM utilization
Correct Answer: D
QUESTION 2
A cloud administrator is switching hosting companies and using the same script that was previously used to deploy VMs
in the new cloud. The script is returning errors that the command was not found. Which of the following is the MOST
likely cause of the script failure?
A. Account mismatches
B. IP address changes
C. API version incompatibility
D. Server name changes
Correct Answer: C
QUESTION 3
A global web-hosting company is concerned about the availability of its platform during an upcoming event. Web traffic
is forecasted to increase substantially during the next week. The site contains mainly static content. Which of the
following solutions will assist with the increased workload?
A. DoH
B. WAF
C. IPS
D. CDN
Correct Answer: D
Reference: https://www.globaldots.com/content-delivery-network-explained
QUESTION 4
A systems administrator disabled TLS 1.0 and 1.1, as well as RC4, 3DES, and AES-128 ciphers for TLS 1.2, on a web
server. A client now reports being unable to access the web server, but the administrator verifies that the server is
online,
the web service is running, and other users can reach the server as well.
Which of the following should the administrator recommend the user do FIRST?
A. Disable antivirus/anti-malware software
B. Turn off the software firewall
C. Establish a VPN tunnel between the computer and the web server
D. Update the web browser to the latest version
Correct Answer: B
QUESTION 5
A systems administrator recently deployed a VDI solution in a cloud environment; however, users are now experiencing
poor rendering performance when trying to display 3-D content on their virtual desktops, especially at peak times. Which
of the following actions will MOST likely solve this issue?
A. Update the quest graphics drivers from the official repository
B. Add more vGPU licenses to the host
C. Instruct users to access virtual workstations only on the VLAN
D. Select vGPU profiles with higher video RAM
Correct Answer: D
Reference:
https://www.cisco.com/c/dam/en/us/solutions/collateral/data-center-virtualization/desktop-virtualization-solutionsvmware-horizon-view/whitepaper-c11-741606.pdf
QUESTION 6
A company recently experienced a power outage that lasted 30 minutes. During this time, a whole rack of servers was
inaccessible, even though the servers did not lose power. Which of the following should be investigated FIRST?
A. Server power
B. Rack power
C. Switch power
D. SAN power
Correct Answer: C
QUESTION 7
A web server has been deployed in a public IaaS provider and has been assigned the public IP address of
72.135.10.100. Users are now reporting that when they browse to the website, they receive a message indicating the
service is
unavailable. The cloud administrator logs into the server, runs a netstat command,
and notices the following relevant output:
Which of the following actions should the cloud administrator take to resolve the issue?
A. Assign a new IP address of 192.168.100.10 to the web server
B. Modify the firewall on 72.135.10.100 to allow only UDP
C. Configure the WAF to filter requests from 17.3.130.3
D. Update the gateway on the web server to use 72.135.10.1
Correct Answer: D
QUESTION 8
An administrator is implementing a private cloud that will be used as a test environment. To limit the number of guests
per subnet to a maximum of 14, the administrator implemented a /20 network. Which of the following should the
administrator use to assign the networks?
A. DHCP
B. Subnet
C. VLAN
D. Gateway
Correct Answer: A
QUESTION 9
A software company recently moved all of its development testing to a public cloud environment. The company primarily
uses IaaS to deploy and test its code. The company needs the software developers to be more agile and efficient when
testing application code. Which of the following backup types should the developers use to BEST ensure the speedy
recovery of a system if it is damaged?
A. Snapshots
B. Full
C. Incremental
D. Differential
Correct Answer: C
QUESTION 10
A cloud architect wants to minimize the risk of having systems administrators in an IaaS compute instance perform
application code changes. The development group should be the only group allowed to modify files in the directory.
Which of the following will accomplish the desired objective?
A. Remove the file write permissions for the application service account.
B. Restrict the file write permissions to the development group only.
C. Add access to the fileshare for the systems administrator\\’s group.
D. Deny access to all development user accounts
Correct Answer: B
QUESTION 11
A software development manager is looking for a solution that will allow a team of developers to work in isolated
environments that can be spun up and torn down quickly. Which of the following is the MOST appropriate solution?
A. Containers
B. File subscriptions
C. Ballooning
D. Software-defined storage
Correct Answer: A
QUESTION 12
Which of the following cloud services is fully managed?
A. IaaS
B. GPU in the cloud
C. IoT
D. Serverless compute
E. SaaS
Correct Answer: C
Reference: https://developers.google.com/iot
QUESTION 13
A company has developed a cloud-ready application. Before deployment, an administrator needs to select a deployment
technology that provides a high level of portability and is lightweight in terms of footprint and resource requirements.
Which of the following solutions will be BEST to help the administrator achieve the requirements?
A. Containers
B. Infrastructure as code
C. Desktop virtualization
D. Virtual machines
Correct Answer: A
Reference: https://blog.netapp.com/blogs/containers-vs-vms/
QUESTION 14
An organization is hosting a DNS domain with private and public IP ranges. Which of the following should be
implemented to achieve ease of management?
A. Network peering
B. A CDN solution
C. A SDN solution
D. An IPAM solution
Correct Answer: D
Reference: https://www.infoblox.com/glossary/ipam-ip-address-management/
QUESTION 15
An organization purchased new servers with GPUs for render farms. The servers have limited CPU resources. Which of
the following GPU configurations will be the MOST optimal for virtualizing this environment?
A. Dedicated
B. Shared
C. Passthrough
D. vGPU
Correct Answer: D
Update the latest valid CompTIA CV0-003 test questions and answers throughout the year.
Upload the latest CV0-003 exam practice questions and CV0-003 PDF for free every month. Get the complete CV0-003 Brain Dumps,
the latest updated exam questions and answers come from Lead4Pass! For information about Lead4pass CV0-003 Dumps (including PDF and VCE),
please visit: https://www.leads4pass.com/cv0-003.html (PDF + VCE)
ps. Get free CompTIA CV0-003 dumps PDF online: https://www.braindump4it.com/wp-content/uploads/2021/07/Lead4pass-CompTIA-Cloud-Plus-CV0-003-Exam-Dumps-Braindumps-PDF-VCE.pdf